Your Medical Device is Cleared. Your Security Job Just Started.
Summary
- FDA clearance marks the beginning, not the end, of cybersecurity responsibilities
- Post-market cybersecurity requires continuous monitoring from six different vulnerability sources
- Manufacturers must respond within 30 days and remediate within 60 days for uncontrolled risks
- Active ISAO participation can provide regulatory enforcement discretion from FDA
- Legacy devices require special planning for end-of-support transitions
- A structured vulnerability management process protects patients and reduces regulatory risk
Introduction: The Post-Market Reality Check
Your medical device just received FDA clearance. The champagne bottles are empty, the team is celebrating, and you’re ready to move on to the next project. But here’s the reality check: your cybersecurity responsibilities have just begun.
According to the FDA’s 2016 Postmarket Management of Cybersecurity guidance, manufacturers must maintain a proactive cybersecurity program throughout the entire product lifecycle. This isn’t just regulatory compliance, it’s about protecting patients from evolving threats that emerge long after your device hits the market.
The threat landscape changes daily. New vulnerabilities are discovered in components you’ve integrated. Hackers develop novel attack methods. Healthcare networks evolve. Your device, frozen in time at its release, must somehow remain secure in this dynamic environment.
Understanding Your Post-Market Cybersecurity Obligations
The FDA expects manufacturers to implement a comprehensive post-market cybersecurity program based on the NIST Framework‘s five core functions: Identify, Protect, Detect, Respond, and Recover. This isn’t optional – it’s embedded in the Quality System regulation under 21 CFR 820.100 for corrective and preventive actions. For more details on overall FDA cybersecurity requirements, see our guide on FDA cybersecurity requirements for medical devices.
Your post-market cybersecurity responsibilities include:
Continuous Monitoring: Actively monitor for vulnerabilities from multiple sources, both internal and external. As noted in AAMI TIR97:2019, this includes monitoring your software bill of materials (SBOM) and all third-party components.
Rapid Response: For vulnerabilities presenting uncontrolled risk to patient safety, you must communicate with customers within 30 days and provide remediation within 60 days. These aren’t suggestions – they’re FDA expectations outlined in the 2016 guidance. Understanding your patch management and security update process is crucial for meeting these timelines.
Shared Responsibility: Post-market cybersecurity isn’t yours alone. You share responsibility with healthcare delivery organizations (HDOs), IT vendors, and security researchers. Clear communication channels and defined roles are essential.
Documentation: Every vulnerability assessment, risk decision, and remediation action must be documented. For PMA devices, this information goes into your annual reports per 21 CFR 814.84.
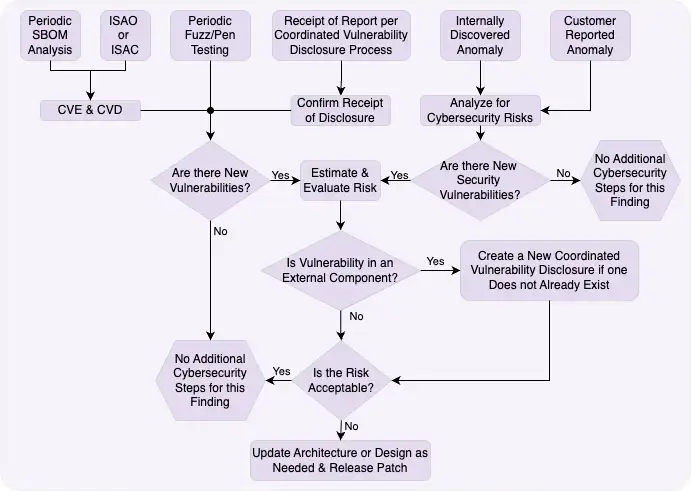
The Six Sources of Vulnerability Discovery
Your vulnerability management process must account for six distinct discovery sources, each requiring specific handling procedures:
Proactive Internal Sources
1. Periodic SBOM Analysis: Regular review of your software bill of materials against vulnerability databases like CVE can identify newly discovered vulnerabilities in components. ANSI/AAMI SW96:2023 emphasizes this as a critical post-production activity. This builds on the secure software development lifecycle established during development.
2. Scheduled Penetration Testing and Fuzzing: Routine security testing reveals vulnerabilities that may have been missed during development. These tests should simulate real-world attack scenarios relevant to your device’s deployment environment. Learn more about how to conduct medical device penetration testing effectively.
3. Internal Anomaly Detection: Your quality system should flag unusual device behavior that might indicate security issues. This includes performance degradation, unexpected communications, or configuration changes. Regular security code reviews can help identify potential vulnerabilities before they’re exploited.
External Sources
4. ISAO/ISAC Participation: Information Sharing and Analysis Organizations/Centers provide early warning of threats affecting medical devices. The FDA strongly encourages participation (more on the benefits later). The Health-ISAC is the primary ISAC for healthcare sector cybersecurity.
5. Customer-Reported Anomalies: Healthcare providers often notice device behavior changes first. Your complaint handling system (21 CFR 820.198) must route potential security issues to your cybersecurity team.
6. Coordinated Vulnerability Disclosure (CVD): Security researchers need a clear path to report vulnerabilities. ISO 29147:2018 provides the framework for establishing your CVD program, including acknowledgment timelines and communication protocols.
Building Your Vulnerability Management Process
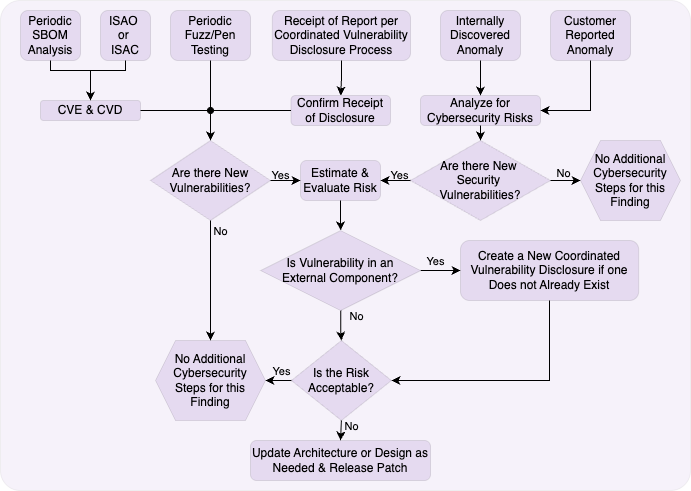
Your vulnerability management process forms the heart of post-market cybersecurity. Let’s walk through each step:
Initial Triage and Assessment
When a vulnerability report arrives, immediate triage determines its validity and potential impact. AAMI TIR97:2019 recommends assembling a cross-functional team including clinical, regulatory, and engineering representatives.
Key questions at this stage:
- Is this a legitimate vulnerability in our device?
- What versions are affected?
- Is this currently being exploited?
- What’s the potential clinical impact?
Risk Evaluation Methodology
Not all vulnerabilities require immediate action. Your risk assessment must consider:
Exploitability: How difficult is it to exploit this vulnerability? Consider required access, technical skill, and available tools. Using CVSS for medical device risk assessment provides a standardized approach.
Severity: What’s the worst-case impact? Could this affect device safety or essential performance?
Mitigations: Are there existing controls that reduce the risk? Can healthcare providers implement compensating controls? Your security architecture should include defense-in-depth strategies.
The FDA distinguishes between controlled and uncontrolled risks. Uncontrolled risks – those with potential for patient harm and no adequate mitigations – trigger the 30/60-day response requirements.
Documentation Requirements
Every vulnerability assessment needs thorough documentation including:
- Discovery source and date
- Affected products and versions
- Risk assessment rationale
- Decision justification
- Remediation timeline
- Customer communications
This documentation supports regulatory submissions and demonstrates your quality system’s effectiveness.
The Critical Decision Points
Your process diagram shows three critical decision points that determine your response path:
Decision 1: Is This a New Vulnerability?
This seems obvious, but duplicate reports are common. Check your vulnerability database before proceeding. If it’s already being addressed, link the new report to the existing case.
Decision 2: Is It in an External Component?
Vulnerabilities in third-party components require different handling. You can’t directly fix someone else’s code, but you’re still responsible for the risk to your device. This triggers your coordinated vulnerability disclosure process with the component vendor.
Decision 3: Is the Risk Acceptable?
This is where your risk assessment pays off. Acceptable risks might receive fixes in the next scheduled update. Unacceptable risks require immediate action.
Remember: “acceptable” doesn’t mean “ignorable.” Document your rationale and implement any available mitigations.
Creating Your Response Playbook
When action is required, having a clear playbook prevents panic and ensures consistent response:
External Component Vulnerabilities
When vulnerabilities exist in third-party components:
- Notify the component vendor through their CVD process
- Assess alternate mitigations while awaiting vendor response
- Prepare customer communications explaining the issue and interim measures
- Plan for component updates including validation and deployment
Patch Development and Deployment
For vulnerabilities in your code:
- Develop the fix following your design controls (21 CFR 820.30)
- Validate thoroughly – rushed patches can introduce new vulnerabilities
- Determine regulatory pathway – does this require a new 510(k) or PMA supplement? See the 2025 update to FDA cybersecurity guidance for latest requirements
- Deploy efficiently using your established update mechanisms. Consider implementing secure software updates and remote update capabilities
Communication Protocols
Clear, timely communication maintains trust and enables healthcare providers to protect patients:
Within 30 days for uncontrolled risks:
- Describe the vulnerability and impact
- Provide interim compensating controls
- Share your remediation timeline
- Establish ongoing communication expectations
Within 60 days:
- Deploy the validated fix
- Provide implementation instructions
- Confirm successful deployment
- Document effectiveness checks per 21 CFR 7.42
Coordination Requirements
Post-market cybersecurity requires extensive coordination:
- Internal teams: Quality, regulatory, engineering, clinical
- External partners: Component vendors, security researchers
- Customers: HDOs, home users, service providers
- Regulatory bodies: FDA, ISAOs, international authorities
Special Considerations for Legacy Devices
Every device eventually becomes “legacy” – but patient safety responsibilities continue. AAMI TIR97:2019 defines key milestones:
End of Life (EOL): You stop selling the device but continue support End of Guaranteed Support (EOGS): Full support can no longer be guaranteed End of Support (EOS): All support ceases
Planning for these transitions requires:
Early Communication
Notify customers at least 18 months before EOGS/EOS. This allows healthcare providers to plan replacements or accept transferred risks.
Risk Transfer Documentation
As support winds down, formally document:
- Remaining vulnerabilities and risks
- Customer responsibilities
- Recommended decommissioning procedures
- Data sanitization requirements
Component Obsolescence
Third-party components often reach end-of-support before your device. Plan for:
- Self-support of critical components
- Architecture updates to remove dependencies
- Clear communication about reduced capabilities
The ISAO Advantage: Your Get-Out-of-MDR-Free Card
Here’s a powerful incentive: active ISAO participation can exempt you from certain FDA reporting requirements under 21 CFR part 806. But “active” is the key word.
Four Criteria for Active Participation
The FDA requires all four criteria be met:
- Membership in an ISAO focused on medical device vulnerabilities
- Documented ISAO operations including privacy protections and business processes
- Information sharing including vulnerability reports and customer communications
- Documented response processes showing how you use ISAO intelligence
For cyber devices specifically, see our guide on what information FDA requires for cyber devices.
Benefits Beyond Compliance
ISAO participation provides:
- Early threat intelligence before public disclosure
- Peer collaboration on similar vulnerabilities
- Coordinated response to industry-wide issues
- Reduced duplicate effort across manufacturers
Documentation Requirements
Maintain objective evidence of your participation:
- Membership agreements and renewal records
- Information shared with the ISAO
- Actions taken based on ISAO alerts
- Process documentation showing ISAO integration
Practical Implementation Tips
Moving from theory to practice, here’s how to build your program:
Staffing Considerations
Post-market cybersecurity requires dedicated resources:
- Security monitoring analyst
- Vulnerability assessment engineer
- Clinical risk assessor
- Regulatory compliance coordinator
Small companies might combine roles, but ensure adequate coverage.
Monitoring Infrastructure
Effective monitoring requires:
- Automated SBOM scanning against vulnerability databases
- Customer portal for security communications
- Incident tracking system integrated with quality system
- Secure researcher communication channel
Consider creating data flow diagrams and architecture security views to visualize your monitoring coverage. For cloud-connected devices, specialized threat modeling for cloud-connected medical devices is essential.
Tool Selection
Essential tools include:
- Vulnerability scanners compatible with your technology stack
- Penetration testing frameworks
- Risk assessment templates
- Communication management systems
QMS Integration
Post-market cybersecurity must integrate with existing quality processes:
- Link to complaint handling (820.198)
- Connect with CAPA system (820.100)
- Integrate with change control (820.70)
- Align with management review (820.20)
Understanding how to implement cybersecurity controls within your QMS ensures compliance. For software-specific considerations, review the differences between SPDF vs IEC 62304.
Measuring Success
Track these metrics to demonstrate program effectiveness:
Response Metrics:
- Time from vulnerability discovery to initial assessment
- Percentage meeting 30/60-day timelines
- Customer communication effectiveness
Quality Metrics:
- Patch defect rates
- Successful deployment percentages
- Repeat vulnerability rates
Program Metrics:
- SBOM completeness and accuracy
- Security training completion
- ISAO participation levels
Report these in PMA annual reports and use them for management review.
Conclusion: Embracing Continuous Security
Post-market cybersecurity isn’t a burden – it’s a competitive advantage. Healthcare providers increasingly evaluate manufacturers’ security programs when making purchasing decisions. A robust post-market program demonstrates your commitment to patient safety beyond the initial sale.
The threat landscape will continue evolving. New attack vectors will emerge. But with a structured vulnerability management process, active monitoring, and strong partnerships, you can maintain device security throughout its lifecycle. Don’t let post-market planning be one of the 5 cybersecurity reasons FDA will refuse your 510(k) for your next submission.
Start by assessing your current capabilities against this framework. Identify gaps. Build your team (including outside firms). Join an ISAO. Most importantly, shift your mindset from “security until launch” to “security for life.”
Your patients depend on it. Your customers expect it. And increasingly, regulators require it.
The champagne from your FDA clearance celebration may have gone flat, but your cybersecurity journey is just beginning.
Key Resources and References
FDA Guidances:
- Postmarket Management of Cybersecurity in Medical Devices (2016)
- Cybersecurity in Medical Devices: Quality System Considerations (2023)
ISAO Information:
Industry Standards:
- ANSI/AAMI SW96:2023 – Standard for medical device security
- AAMI TIR97:2019 – Principles for medical device security—Postmarket risk management
- ISO/IEC 29147:2018 – Information technology — Security techniques — Vulnerability disclosure
CVD Resources:
Tools and Templates: