Cybersecurity Traceability Matrices FDA Will Expect to See in Your Medical Device Submission
Summary
In this article, you’ll learn:
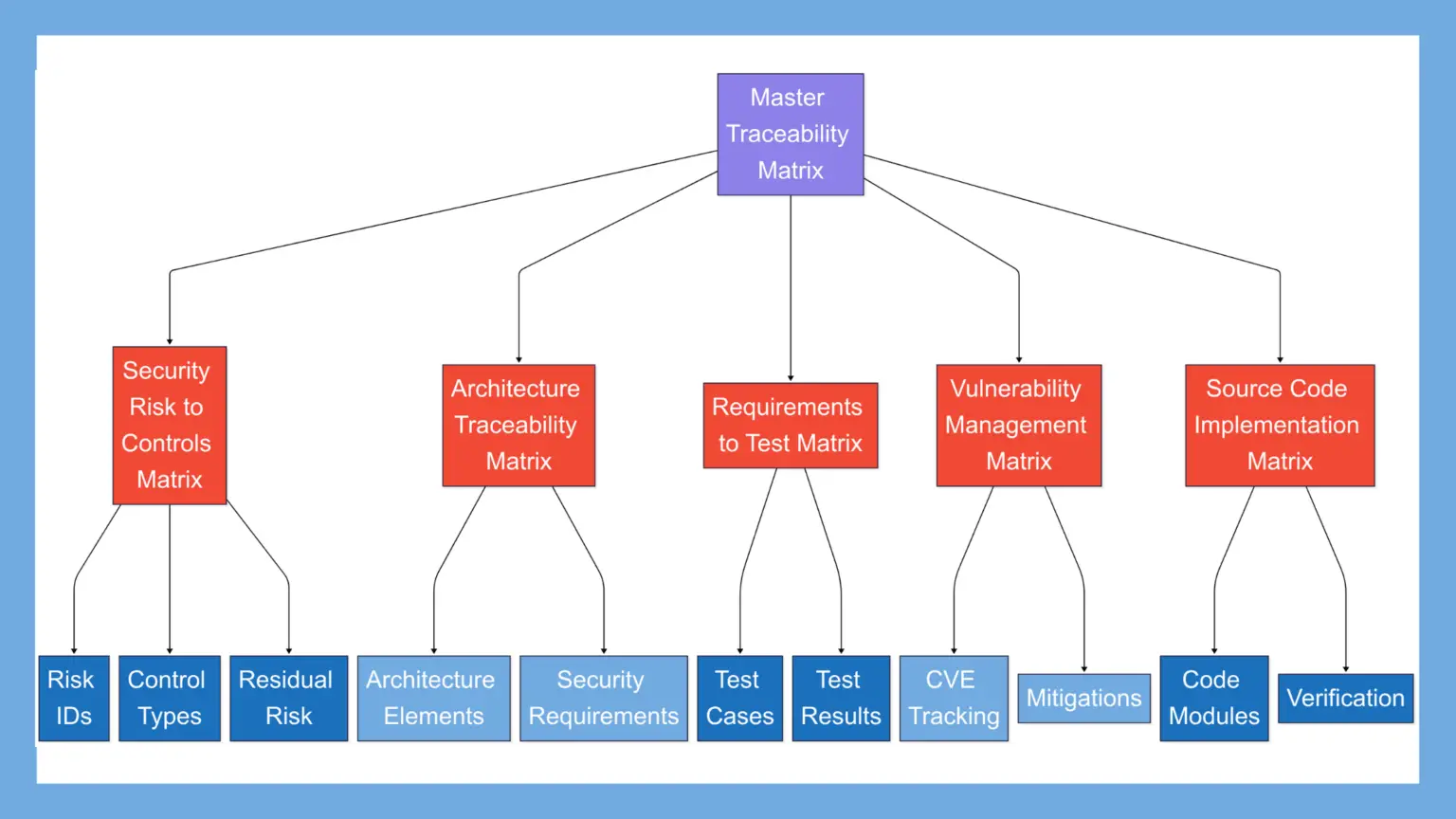
- The master cybersecurity traceability matrix FDA expects in your submission
- Five essential supporting matrices that demonstrate comprehensive security
- How to structure each matrix for clear regulatory review
- Best practices to avoid common submission issues
- Why complete traceability is critical for FDA approval
Introduction
A cybersecurity traceability matrix is more than just documentation—it’s your roadmap showing FDA how you’ve systematically addressed security risks throughout your medical device development. With FDA’s 2023 cybersecurity guidance (updated in June 2025 for clarity) and Section 524B requirements now in effect, comprehensive traceability has become essential for demonstrating that your device is reasonably secure and effective.
The FDA expects manufacturers to provide clear traceability linking security risks to controls, requirements to tests, and vulnerabilities to mitigations. Without proper cybersecurity traceability matrices, reviewers struggle to understand how you’ve managed cybersecurity risks across your device’s lifecycle. The June 2025 update reinforced that these requirements apply to ANY device with software—including firmware or programmable logic—regardless of internet connectivity. Understanding FDA cybersecurity requirements for medical devices is essential before building your traceability framework.
The Master Traceability Matrix in Your Cybersecurity Summary Report
The most critical traceability requirement appears in FDA’s cybersecurity guidance: manufacturers must “provide traceability between the threat model, cybersecurity risk assessment, SBOM, and testing documentation.” This master matrix serves as the cornerstone of your cybersecurity submission.
Core Elements of the Master Matrix
Your master traceability matrix must connect four essential elements:
1. Threat Model → Risk Assessment: Each identified threat must map directly to specific risk assessments in your documentation. This linkage shows FDA reviewers that you’ve systematically analyzed every potential threat and evaluated its impact on your device. The traceability demonstrates that no threats were overlooked and that each one received appropriate risk evaluation based on exploitability and potential patient harm. Proper threat modeling for medical devices forms the foundation of this critical linkage.
2. Risk Assessment → SBOM Components: Your matrix must clearly link each identified risk to the specific software components that introduce or are affected by that risk. This connection is particularly important for third-party software, where vulnerabilities may already exist in components you’ve incorporated. The FDA’s 2025 clarification emphasized that SBOM requirements now include better-defined expectations for component documentation and vulnerability tracking.
3. SBOM Components → Vulnerability Assessments: Every component in your Software Bill of Materials needs traceability to its vulnerability assessment. This includes mapping to known CVEs, cross-referencing with CISA’s Known Exploited Vulnerabilities catalog, and documenting your assessment methodology. The matrix should show how you’ve evaluated each component for security weaknesses and what determinations you’ve made about exploitability.
4. All Elements → Testing Documentation: The final critical linkage connects everything to your verification activities. This demonstrates that you haven’t just identified and assessed risks—you’ve actually tested your mitigations. Include specific test case IDs, test protocols, execution records, and results. This comprehensive testing traceability proves your security controls work as intended.
Example Master Matrix Structure
| Threat ID | Threat Description | Risk ID | Risk Assessment | SBOM Component | Vulnerabilities | Test Case ID | Test Results |
|---|---|---|---|---|---|---|---|
| TH-001 | Network-based attack exploiting unencrypted communication channels | RA-001 | High exploitability due to wireless interface, Medium patient impact if data intercepted | OpenSSL v1.1.1n | CVE-2023-0286, CVE-2023-0215 | TC-SEC-001, TC-SEC-002, TC-SEC-003 | Pass – TLS 1.3 implemented and verified |
| TH-002 | Unauthorized firmware update through USB interface | RA-002 | Low exploitability (requires physical access), High patient impact if malicious firmware installed | Boot loader v2.0 | None identified | TC-SEC-015, TC-SEC-016 | Pass – Signature verification confirmed |
| TH-003 | Denial of service through malformed network packets | RA-003 | Medium exploitability, Low patient impact (fail-safe mode activated) | TCP/IP Stack v3.2 | CVE-2023-4567 | TC-SEC-025, TC-SEC-026 | Pass – Input validation effective |
This master matrix becomes your executive summary, allowing FDA reviewers to quickly understand your security posture and navigate to detailed documentation.
The Security Risk to Controls Traceability Matrix
Following AAMI SW96 and TIR57 requirements, this matrix links each identified security risk to its corresponding controls. FDA reviewers use this to verify you’ve addressed all identified risks appropriately.
Key Elements to Include
Risk Identification: Each risk must have a unique identifier that remains consistent throughout all documentation. Include a clear risk description that explains the vulnerability, threat actor, and potential impact. The initial risk score should reflect the risk level before any controls are applied, using your documented scoring methodology.
Control Implementation: Document the specific security controls you’ve implemented to address each risk. Classify each control by type—preventive controls stop threats before they occur, detective controls identify when threats are attempted, and corrective controls limit damage after an incident. Specify where controls are implemented: in the architecture design, source code, operational procedures, or user documentation.
Residual Risk: After controls are applied, document the new risk score and your acceptability determination. If residual risk remains above acceptable thresholds, document additional mitigations or compensating controls. Include rationale for why certain residual risks may be accepted, particularly when they involve user responsibilities or environmental controls.
Integration with ISO 14971
Safety and Security Convergence: Your security risk matrix must demonstrate clear integration with your overall risk management process per ISO 14971. When security risks could impact patient safety, show how they’re evaluated in both contexts. For example, a denial-of-service attack that could delay critical therapy must be assessed for both its security severity and its potential to cause patient harm.
Risk Evaluation Consistency: Use consistent risk scoring methodologies between safety and security assessments where possible. Document any differences in approach and explain why they’re necessary. Show how combined risks (where security vulnerabilities could trigger safety hazards) are managed holistically.
Security Architecture Traceability Matrix
FDA’s guidance emphasizes that security architecture views must establish “traceability of architecture elements to user and medical device system security requirements.” This matrix demonstrates how your design implements security at the architectural level.
Required Mappings
Architecture Elements → Security Requirements: Every security-relevant component in your architecture must trace to one or more security requirements. This includes network interfaces mapping to communication security requirements, authentication modules linking to access control requirements, and data storage components connecting to confidentiality requirements. The traceability proves that your architecture directly addresses identified security needs.
Security Controls → Architecture Implementation: Show precisely where and how each security control is implemented within your architecture. For authentication mechanisms, identify the specific modules and interfaces involved. For encryption, show where cryptographic functions are called and how keys are managed. For network segmentation, illustrate how different security domains are isolated and what controls exist at boundaries.
Example Format
| Architecture Element | Security Requirement | Implementation Details | Verification Method |
|---|---|---|---|
| Network Interface Module | REQ-SEC-008: All external communications shall use authenticated encryption | TLS 1.3 with mutual authentication, minimum 256-bit keys, certificate pinning implemented | Protocol analysis, penetration testing, certificate validation testing |
| User Authentication Service | REQ-SEC-001: Multi-factor authentication required for administrative access | TOTP with 6-digit codes + biometric verification, 3-attempt lockout, 30-second timeout | Unit testing, integration testing, usability validation |
| Data Storage Engine | REQ-SEC-012: Patient data at rest shall be encrypted | AES-256-GCM with key derivation from TPM, automatic key rotation every 90 days | Cryptographic validation, key management testing |
| Update Manager | REQ-SEC-022: Software updates shall be cryptographically signed | RSA-4096 signatures with certificate chain validation, rollback protection | Update simulation testing, signature verification |
Security Requirements to Test Cases Matrix
This matrix proves you’ve verified every security requirement through appropriate testing. It’s essential for demonstrating compliance with design controls under 21 CFR 820.30(g) and is a key focus area during FDA review.
Critical Components
Requirement Coverage: Every security requirement must have corresponding test cases that fully verify its implementation. Include both positive testing (confirming the control works as intended) and negative testing (ensuring the control properly rejects invalid inputs or attacks). Document edge cases and error conditions to show comprehensive coverage.
Test Methodology: Specify the type of testing performed for each requirement. Unit tests verify individual components implement security controls correctly. Integration tests confirm that security controls work properly when components interact. System tests validate end-to-end security across the entire device. Penetration testing and fuzz testing attempt to bypass controls to verify their effectiveness—these independent security assessments are particularly important for FDA submissions.
Traceability Elements: Create clear linkages from each requirement ID to multiple test case IDs that verify it. Connect test protocols to their execution records, showing when tests were run and by whom. Link pass/fail criteria to actual results, including any deviations or anomalies discovered during testing.
Example Structure
| Security Requirement | Test Case IDs | Test Type | Test Description | Pass Criteria | Results |
|---|---|---|---|---|---|
| REQ-SEC-001: Multi-factor authentication | TC-SEC-101, TC-SEC-102, TC-SEC-103 | Unit, Integration, System | Verify TOTP generation, biometric capture, integration with access control | Successful authentication only with both factors, lockout after failures | Pass – All criteria met |
| REQ-SEC-008: Encrypted communications | TC-SEC-201 through TC-SEC-210 | Unit, Integration, Penetration | TLS handshake, cipher suite negotiation, certificate validation, MITM resistance | Only TLS 1.3 accepted, weak ciphers rejected, invalid certificates blocked | Pass – No vulnerabilities found |
Vulnerability Management Traceability
With increasing focus on software supply chain security, FDA expects comprehensive vulnerability tracking and mitigation documentation throughout your device’s components.
SBOM Component Vulnerability Mapping
Comprehensive Component Analysis: For each third-party component in your SBOM, document all known vulnerabilities at the time of submission. Include CVE identifiers, CVSS scores, and publication dates. Cross-reference each vulnerability with CISA’s Known Exploited Vulnerabilities catalog to identify those actively targeted in the wild.
Exploitability Assessment: Document how each vulnerability could potentially be exploited in your specific implementation. Consider your device’s architecture, network exposure, and security controls. Some vulnerabilities may not be exploitable due to your configuration or compensating controls—document this analysis clearly.
Impact Analysis: Assess how exploitation of each vulnerability would affect your device’s operation, patient safety, and data security. Consider both direct impacts (device malfunction) and indirect impacts (data breach leading to privacy violations). Document which device functions could be affected and what the clinical consequences might be.
Mitigation Traceability
| Vulnerability ID | Component | Risk Assessment | Mitigation Strategy | Verification |
|---|---|---|---|---|
| CVE-2023-12345 | libcurl 7.81.0 | Medium risk – requires local network access, could cause DOS | Updated to patched version 7.81.1, implemented rate limiting | Regression testing confirmed functionality, penetration test verified fix |
| CVE-2023-67890 | Legacy imaging driver | High risk – remote code execution possible | Cannot update due to hardware dependency; implemented network isolation, strict input validation, and monitoring | Penetration testing confirmed compensating controls effective |
| CVE-2024-11111 | JSON parser library | Low risk – information disclosure only, no patient data exposed | Accepted risk with monitoring, planned update in next release | Security assessment documented, monitoring alerts configured |
Unresolved Anomalies
Security Anomaly Documentation: Following FDA’s guidance on unresolved anomalies, document any security-related issues that remain in your device at the time of submission. Include the anomaly description, discovery method, and security impact assessment. Explain why the anomaly wasn’t resolved (e.g., low risk, significant redesign required, third-party dependency).
Compensating Controls: For each unresolved security anomaly, document what compensating controls you’ve implemented. These might include additional monitoring, restricted functionality, user warnings, or environmental controls. Show how these compensations reduce risk to acceptable levels.
Residual Risk Acceptance: Provide clear rationale for accepting any residual security risks. Include your risk scoring, comparison to similar accepted risks, and any planned future mitigations. Document management approval for risk acceptance decisions.
Source Code Implementation Traceability
Demonstrating that security controls are properly implemented in code is crucial for FDA review. This traceability supports your claim that the device is “built secure” from the ground up.
Key Mappings
Security Controls → Code Modules: Create explicit mappings showing which source code modules implement each security control. Include file names, function names, and line numbers where key security logic resides. For example, authentication controls might map to auth_manager.c, specifically the validate_user() and check_credentials() functions.
Library and API Usage: Document how you’re using security libraries and APIs correctly. Show which cryptographic libraries you’re using for encryption, which functions you call, and how you handle keys. Include configuration parameters and initialization sequences. This proves you’re not just including security libraries but using them properly.
Custom Security Implementations: If you’ve implemented any custom security controls, provide extra detail on the implementation. Include design rationale, testing approach, and any security reviews performed. Custom cryptography or authentication schemes receive particular scrutiny and need comprehensive documentation.
Verification Coverage
Static Analysis Linkage: Connect static analysis findings to specific code modules and security controls. Show how you’ve addressed any security warnings or weaknesses identified. Document which static analysis tools you used and their configuration.
Code Review Traceability: Link security-focused code reviews to the modules containing security controls. Document who performed reviews, what issues were found, and how they were resolved. Include evidence of reviews by security-experienced developers.
Test Coverage Metrics: Provide code coverage metrics specifically for security-related code. Show that your security controls have been thoroughly tested, including error paths and exception handling. Link coverage reports to your test execution records.
CWE Category Integration
Weakness Identification: Map any identified code weaknesses to Common Weakness Enumeration (CWE) categories. Show how your coding practices address common weaknesses like buffer overflows (CWE-120), SQL injection (CWE-89), or improper authentication (CWE-287).
Remediation Tracking: Document how each identified weakness was remediated or why it remains (with compensating controls). Include verification that remediations were effective and didn’t introduce new weaknesses.
Best Practices for Creating Effective Traceability Matrices
Use Consistent Identifiers
Establish a Numbering Convention: Create a systematic approach to identifying all elements across your documentation. Use prefixes that clearly indicate the element type: TH- for threats, RA- for risk assessments, REQ-SEC- for security requirements, TC-SEC- for security test cases. This consistency helps reviewers navigate your documentation and verify completeness.
Maintain Identifier Persistence: Once assigned, identifiers should never change, even if the item is modified. If requirements evolve, update the description but keep the ID. This maintains traceability through design changes and helps with configuration management.
Cross-Reference Systematically: Every identifier mentioned in one document should be traceable to its definition in another. Create a master index showing where each identifier is defined and where it’s referenced.
Leverage Automation Tools
Requirements Management Systems: Manual maintenance of traceability matrices becomes error-prone as systems grow complex. Use dedicated requirements management tools that can automatically maintain linkages, flag orphaned items, and generate traceability reports. These tools can integrate with your development environment to maintain live traceability.
Continuous Integration Benefits: Integrate traceability checking into your CI/CD pipeline. Automated scripts can verify that all requirements have test cases, all risks have controls, and all controls are implemented. This catches traceability gaps early, before they become FDA review findings.
Version Control Integration: Maintain your traceability matrices in version control alongside your design documentation. This provides history of how traceability evolved and helps explain design decisions during FDA review.
Maintain Living Documents
Regular Update Cycles: Traceability isn’t created once at the end of development—it must be maintained throughout. Establish regular review cycles where you verify all linkages remain accurate. Update matrices when new vulnerabilities are discovered, requirements change, or test cases are added.
Change Impact Analysis: When making design changes, use traceability to perform impact analysis. If a requirement changes, trace forward to find all affected test cases. If a new vulnerability is discovered, trace to affected components and their controls.
Post-Market Maintenance: Your traceability matrices remain valuable after FDA approval. They help you quickly assess the impact of new vulnerabilities, plan updates efficiently, and document changes for FDA reporting.
Common FDA Review Issues to Avoid
Incomplete Linkages: FDA reviewers frequently find gaps in traceability—requirements without test cases, risks without documented controls, or controls without implementation evidence. Perform systematic reviews to find and fix these gaps before submission. Use tools to automatically identify orphaned items.
Inconsistent Information: Information inconsistencies between documents create confusion and slow reviews. Common problems include ID mismatches (REQ-SEC-001 in one document called REQ-001 in another), version misalignment (SBOM shows version 2.1 but test results reference version 2.0), and outdated information (vulnerability assessment from six months ago not updated).
Insufficient Detail: Generic descriptions don’t provide the specificity FDA needs. Instead of “encryption implemented,” specify “AES-256-GCM encryption implemented in crypto_module.c using OpenSSL 3.0.8, keys generated by hardware RNG, key rotation every 90 days.” Provide enough detail for reviewers to understand your implementation without reading source code.
How Complete Traceability Supports FDA Review
Demonstrates QS Regulation Compliance
Design Control Evidence: Comprehensive traceability directly demonstrates compliance with 21 CFR 820.30 design controls. Your matrices show that design inputs (security requirements) trace to design outputs (implementation), verification activities confirm the design meets requirements, and validation demonstrates the device meets user needs in its intended environment.
Change Control Documentation: When design changes occur, traceability helps document the impact and verification of changes. This supports compliance with change control requirements and helps FDA understand how changes were managed. For devices seeking 510(k) clearance, comprehensive traceability is essential for demonstrating substantial equivalence.
Enables Efficient Review
Navigation Assistance: Well-organized matrices serve as a roadmap for FDA reviewers, helping them quickly locate relevant information. Instead of searching through hundreds of pages, reviewers can follow traceability links to find specific evidence.
Completeness Verification: Traceability matrices allow reviewers to systematically verify that all security aspects have been addressed. They can quickly identify any gaps in your security approach and focus their detailed review appropriately.
Risk-Based Review Focus: By clearly showing high-risk areas and their controls, traceability helps reviewers prioritize their efforts. They can spend more time on critical security controls and less time on well-documented, lower-risk areas.
Supports Substantial Equivalence
Clear Comparison Framework: For 510(k) submissions, traceability matrices facilitate comparison with predicate devices. You can show which security controls are equivalent, which are improved, and justify any differences.
Difference Documentation: When your device has different security features than the predicate, traceability helps document that these differences don’t affect safety and effectiveness. Link new controls to the risks they address and show equivalent risk mitigation.
Facilitates Post-Market Updates
Vulnerability Response Efficiency: When new vulnerabilities are discovered post-market, traceability helps you quickly identify affected components, assess impact, and plan mitigations. This supports faster response times and better patient safety.
Change Documentation: Traceability matrices make documenting post-market changes straightforward. You can clearly show what changed, why, and how it was verified, supporting FDA reporting requirements.
Lifecycle Management: Good traceability supports efficient device lifecycle management, from initial design through end-of-support. It helps plan updates, assess risks, and maintain security throughout the device’s market life.
Conclusion
The master cybersecurity traceability matrix—linking threat models, risk assessments, SBOMs, and testing—forms the backbone of your FDA submission. Supporting matrices for security controls, architecture, requirements, vulnerabilities, and code implementation provide the detailed evidence FDA needs to evaluate your device’s security posture.
Remember that traceability isn’t just a regulatory checkbox—it’s a powerful tool that demonstrates your systematic approach to building security into your device. Well-executed traceability matrices tell a clear story of how you’ve identified threats, assessed risks, implemented controls, and verified their effectiveness.
The FDA’s June 2025 guidance update reinforced these expectations while clarifying that they apply to any device containing software. Start building your traceability framework early in development, maintain it throughout the product lifecycle, and use it as a living tool for security management. Your FDA reviewers—and ultimately your device’s security—will benefit from this disciplined approach.
Additional Resources
- FDA Cybersecurity in Medical Devices Guidance (Updated June 2025)
- ANSI/AAMI SW96:2023 Standard
- ISO 14971:2019 Medical Device Risk Management
- AAMI TIR57:2016/(R)2023 Principles for Medical Device Security
- FDA Cybersecurity Requirements for Medical Devices – Complete Guide
Ready to Build Your Cybersecurity Traceability?
Creating comprehensive cybersecurity traceability requires expertise in both medical device development and regulatory requirements. CyberMed specializes in preparing all 12 cybersecurity attachments required for FDA 510(k) submissions, including complete traceability matrices that meet FDA expectations.
Our services include:
- Comprehensive threat modeling and risk assessment
- SBOM generation and vulnerability analysis
- Security architecture documentation
- Complete traceability matrix development
- Penetration testing and fuzz testing to verify security controls
Contact our team of medical device cybersecurity experts to ensure your submission meets FDA requirements the first time.
Keywords: cybersecurity traceability matrix, FDA medical device cybersecurity, medical device security documentation, FDA cybersecurity submission, security risk traceability, SBOM traceability, medical device threat modeling, FDA cybersecurity guidance 2025