FDA cybersecurity requirements apply to any medical device that has software. This surprises many MedTech executives. They assume that only cloud-connected medical devices have cybersecurity requirements. However, FDA’s guidance clearly states that’s not the case.
With that said, as medical devices become increasingly connected and software-dependent, cybersecurity has emerged as a critical aspect of medical device safety and effectiveness. If your medical device incorporates software components, you must comply with the FDA’s cybersecurity requirements throughout the product lifecycle. This comprehensive guide walks through the essential phases and documentation requirements for ensuring compliance.
Understanding the FDA Cybersecurity Framework
The FDA’s approach to medical device cybersecurity is divided into two main categories:
- Pre-market requirements – addressing security during development
- Post-market responsibilities – maintaining security after deployment
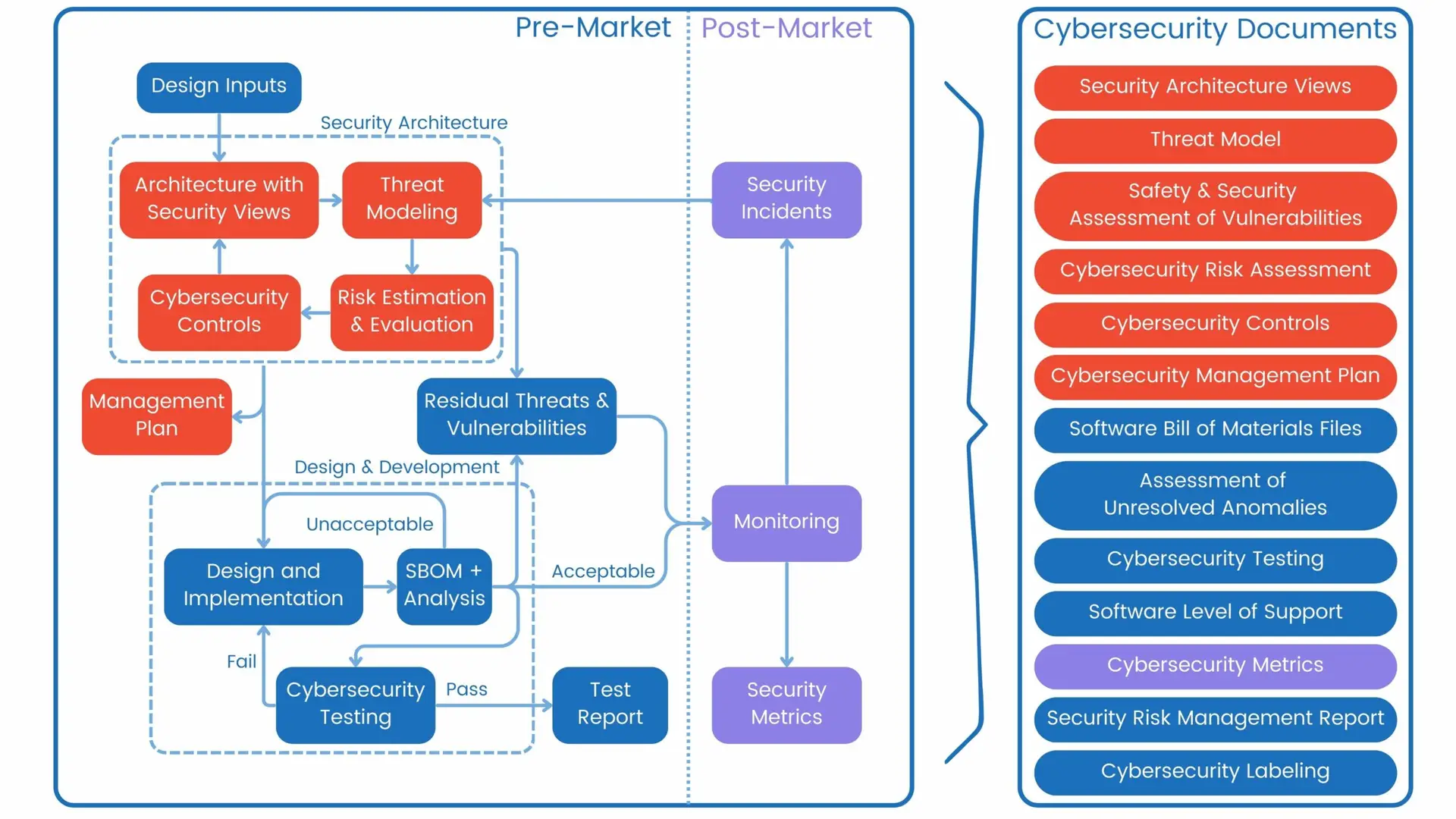
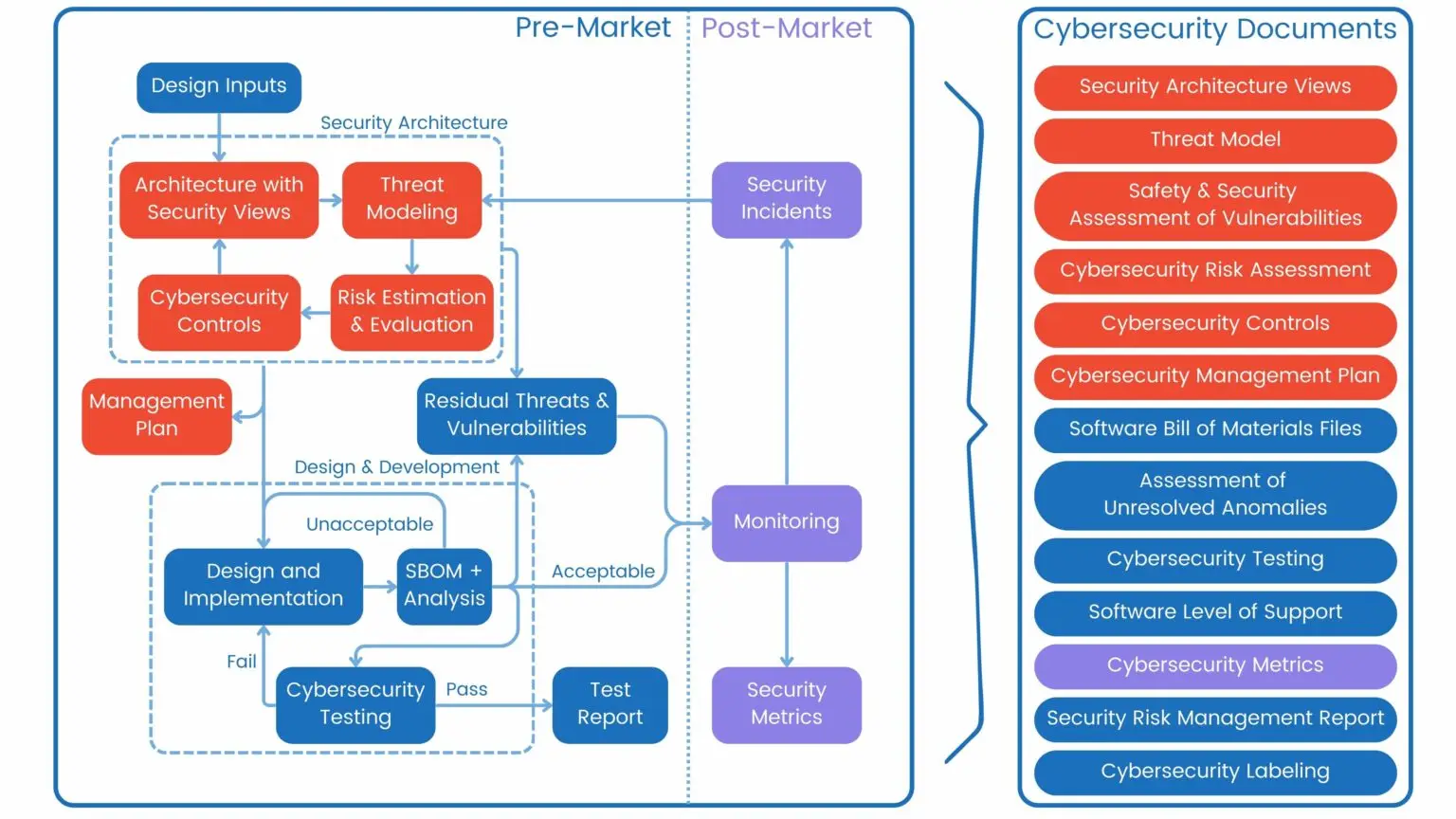
To effectively manage pre-market requirements, we recommend splitting the process into two distinct phases: Security Architecture and Design & Development. This structured approach ensures comprehensive coverage of all security aspects while maintaining clear focus during each development stage.
Phase 1: Security Architecture
The Security Architecture phase forms the foundation of your device’s cybersecurity strategy. During this phase, you’ll need to:
System Architecture
Start by developing a comprehensive system architecture that considers security from the ground up. This should include all components, interfaces, and data flows within your medical device system.
Security Views
Create detailed security views that illustrate how your system implements security controls and protects against potential threats. These views should clearly demonstrate your security architecture’s effectiveness to FDA reviewers.
Threat Modeling
Conduct thorough threat modeling to identify potential security vulnerabilities and attacks that could affect your device. This process should:
- Map out all potential attack surfaces
- Identify possible threat actors and their capabilities
- Document potential attack scenarios
- Consider both internal and external threats
Risk Evaluation
For each identified threat:
- Estimate the likelihood of occurrence
- Assess potential impact on device safety and effectiveness
- Calculate overall risk levels
- Prioritize threats based on risk assessment
Security Controls
Based on your threat modeling and risk evaluation:
- Determine appropriate security controls to mitigate identified risks
- Ensure controls are proportional to risk levels
- Consider both technical and administrative controls
- Document control selection rationale
Security Management Planning
Develop a comprehensive security management plan that outlines:
- Roles and responsibilities
- Security processes and procedures
- Incident response protocols
- Ongoing monitoring requirements
Phase 2: Design & Development
With the security architecture established, the Design & Development phase focuses on implementation and verification:
Software Implementation
Develop your software following secure coding practices and implementing the security controls defined in your architecture phase.
Software Bills of Materials (SBOMs)
- Generate comprehensive SBOMs for all software components
- Include both custom and third-party software
- Document all dependencies and their versions
- Maintain SBOM accuracy throughout development
Anomaly Analysis
- Review SBOMs for known vulnerabilities
- Identify potential security issues in third-party components
- Assess the impact of discovered anomalies on your system
- Document findings and mitigation strategies
Security Testing
Perform thorough cybersecurity testing, including:
- Vulnerability scanning
- Penetration testing
- Security control verification
- Integration testing with security features
- Documentation of test results and findings
Residual Risk Management
- Address identified security risks through remediation
- Document any accepted residual risks
- Provide justification for accepting residual risks
- Ensure residual risk levels meet FDA requirements
Post-Market Activities
Your cybersecurity responsibilities continue after device deployment:
Continuous Monitoring
- Monitor for new threats and vulnerabilities
- Track security metrics and trends
- Evaluate emerging security risks
- Maintain awareness of industry security developments
Incident Management
- Document security incidents and responses
- Communicate incidents to relevant stakeholders
- Address security issues promptly
- Learn from incidents to improve security
Software Maintenance
- Develop and distribute patches and updates
- Maintain secure update mechanisms
- Verify update integrity and authenticity
- Track update deployment and success rates
Security Metrics
- Define and track relevant security metrics
- Monitor security control effectiveness
- Measure incident response performance
- Track vulnerability management metrics
Required Documentation
The FDA requires comprehensive documentation of your cybersecurity efforts. Prepare and maintain the following documents throughout development:
- Security Architecture Views
- Threat Model
- Safety & Security Assessment of Vulnerabilities
- Cybersecurity Risk Assessment
- Cybersecurity Controls
- Cybersecurity Management Plan
- Software Bill(s) of Materials
- Assessment of Unresolved Anomalies
- Cybersecurity Testing Report
- Software Level of Support
- Cybersecurity Metrics
- Security Risk Management Report
- Cybersecurity Labeling
Conclusion
Meeting FDA cybersecurity requirements requires a systematic approach and thorough documentation throughout your medical device’s lifecycle. By following this structured process and maintaining comprehensive documentation, you can demonstrate your commitment to device security and streamline your FDA submission process.
Remember that cybersecurity is an ongoing process, not a one-time effort. Maintaining strong security practices and documentation throughout your device’s lifecycle is essential for both regulatory compliance and patient safety.
Note: This guide provides a general framework for FDA cybersecurity compliance. Specific requirements may vary based on your device’s risk level and intended use. Consider consulting with regulatory experts for guidance specific to your situation.