Balancing Security Controls with Usability in Medical Devices: A Risk-Based Approach
Summary
When an infusion pump requires three authentication steps in an emergency situation, those extra seconds could mean the difference between life and death. The tension between cybersecurity controls and clinical workflows represents one of the most critical challenges in modern medical device design. This comprehensive guide explores how manufacturers can balance security controls with usability in medical device development through collaboration and risk-based approaches that protect patients while maintaining clinical efficiency.
What you’ll learn from this article:
- How to identify and address the unique constraints that make medical device security different from traditional IT security
- A systematic approach to conducting dual risk assessments for both security and usability concerns
- Practical implementation strategies for building security into clinical workflows without compromising patient care
- Specific regulatory requirements and documentation strategies for FDA submissions
- Real-world examples of successful security solutions that maintain clinical usability
- Best practices for emergency access provisions and break-glass procedures
Introduction
The healthcare industry faces an unprecedented challenge in medical device cybersecurity usability. As medical devices become increasingly connected and sophisticated, the need for robust cybersecurity controls has never been greater. However, these security measures must coexist with the life-critical nature of healthcare delivery, where seconds can determine patient outcomes.
According to FDA cybersecurity guidance, “cybersecurity threats to the healthcare sector have become more frequent and severe,” making security an essential component of device safety and effectiveness. Yet the unique constraints of medical devices create a complex balancing act. Unlike traditional IT systems, medical devices operate in environments where user capabilities vary dramatically, time pressures are extreme, and the consequences of both security failures and usability barriers can be life-threatening.
The challenge extends beyond technical implementation to fundamental design philosophy. As the FDA emphasizes, effective cybersecurity relies upon security being “built in” to a device, not “bolted on” after design completion. This principle becomes even more critical when considering clinical usability, as security controls must be seamlessly integrated into existing clinical workflows without creating dangerous delays or user errors.
Understanding the Core Challenge
Unique Constraints of Medical Devices
Medical devices present fundamentally different security challenges compared to conventional IT systems. The AAMI SW96 standard identifies several key differentiating characteristics that directly impact medical device cybersecurity usability. These devices require risk-benefit analysis within their specific context of use, focus on hazard analysis rather than pure threat prevention, and must undergo testing that prioritizes minimizing risk of injury or damage above all other considerations.
Clinical environment considerations: Medical devices operate in high-stress, time-sensitive environments where users may be dealing with life-or-death situations. Emergency departments, operating rooms, and intensive care units present unique challenges where traditional authentication methods may be impractical or dangerous. The lighting conditions, noise levels, and space constraints all influence how security controls can be effectively implemented.
Time-critical operations: Unlike business IT systems where a few extra seconds for authentication rarely matter, medical devices often operate in scenarios where delays can have severe consequences. An infusion pump that requires complex authentication during a cardiac arrest, or a ventilator that locks out during a respiratory crisis, can directly impact patient survival. This temporal constraint fundamentally changes how security controls must be designed and implemented.
User capability variations: Healthcare professionals operate under varying levels of stress, fatigue, and time pressure. The MITRE Playbook for Threat Modeling Medical Devices specifically notes that “password-based authentication might not be appropriate in environments or use cases in which the patient’s memory or dexterity might be reduced, or when access time is critical.” This reality demands security solutions that accommodate human factors while maintaining protection.
Security Requirements Evolution
The threat landscape for medical devices continues to evolve rapidly, with cybersecurity risks becoming more sophisticated and targeted. The FDA’s cybersecurity guidance emphasizes that “cybersecurity risks evolve over time and as a result, the effectiveness of cybersecurity controls may degrade as new risks, threats, and attack methods emerge.” This dynamic environment requires security controls that can adapt without compromising clinical workflows.
Regulatory expectations: Under Section 524B of the FD&C Act, manufacturers must demonstrate that their cybersecurity controls provide reasonable assurance of safety and effectiveness. This includes implementing management, technical, and operational controls across the entire medical device system. The FDA specifically requires that cybersecurity considerations be integrated into design controls from the earliest stages of development.
Authentication needs: Modern medical devices require various levels of authentication depending on their risk profile and clinical context. However, traditional multi-factor authentication approaches may not be appropriate for emergency situations. The challenge lies in creating tiered authentication systems that provide appropriate security while maintaining clinical accessibility.
Usability Requirements in Clinical Context
Clinical usability extends far beyond simple ease of use. In medical device contexts, usability directly impacts patient safety and clinical outcomes. The FDA guidance on human factors emphasizes that usability engineering must be integrated throughout the design process, with particular attention to how security controls affect clinical workflows.
Clinical workflow efficiency: Healthcare delivery depends on smooth, efficient workflows that minimize interruptions and delays. Security controls that disrupt these workflows can create dangerous bottlenecks or encourage workaround behaviors that actually reduce overall security. Successful medical device cybersecurity usability requires deep understanding of clinical processes and careful integration of security measures.
Emergency access provisions: Perhaps no aspect of medical device security is more critical than emergency access. The AAMI SW96 standard specifically addresses this challenge, noting that “emergency device access may mean healthcare delivery organizations need to have access without a prior relationship with the patient or the medical device.” This requirement demands sophisticated security architectures that can distinguish between legitimate emergency access and potential threats.
Risk-Based Design Approach
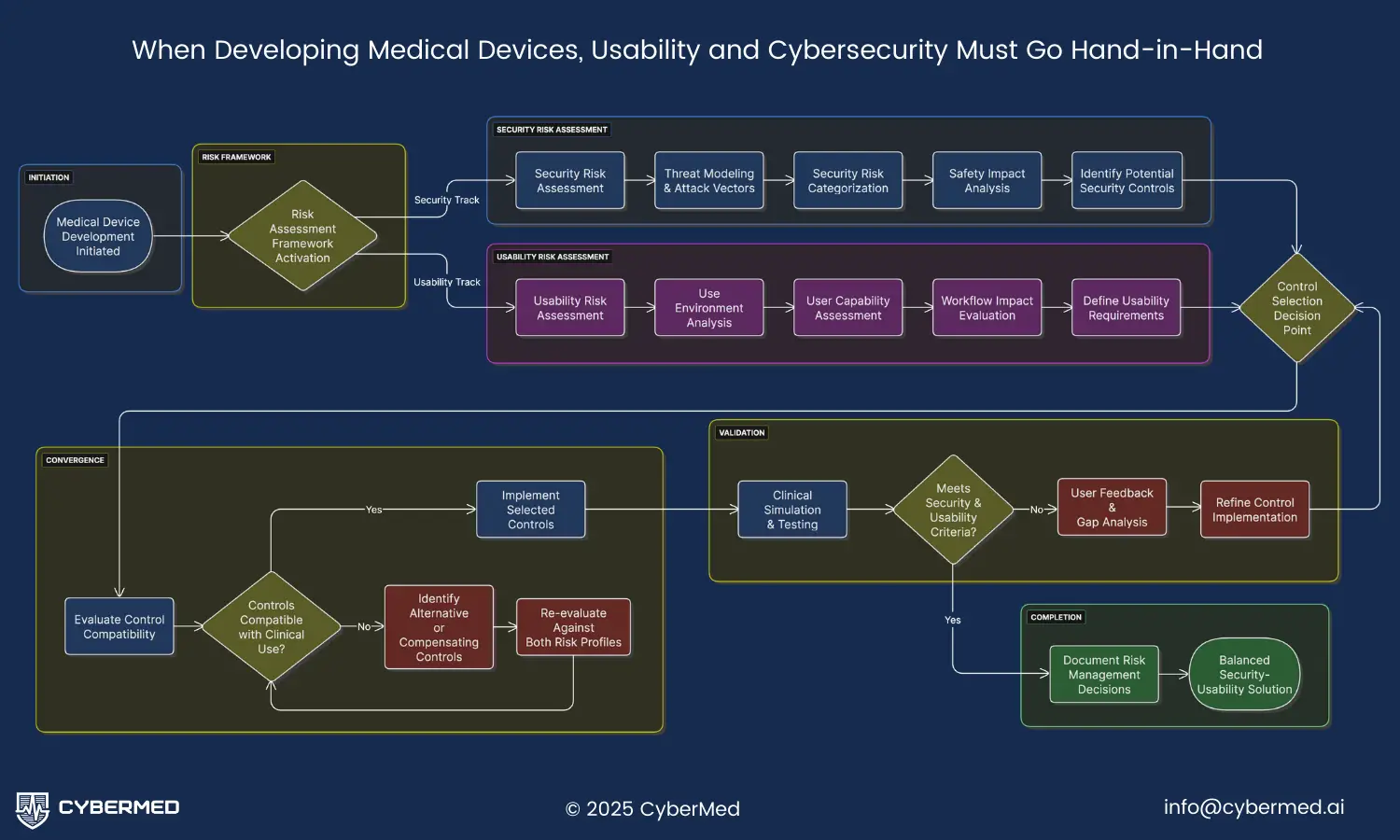
Security Risk Assessment Framework
Effective medical device cybersecurity usability begins with comprehensive risk assessment that considers both security threats and clinical impacts. The FDA recommends following established frameworks like NIST SP 800-30 for conducting security risk assessments, but these must be adapted for the unique constraints of medical devices.
Threat modeling specifics: Medical device threat modeling must consider not only traditional cybersecurity threats but also the clinical context in which these threats might manifest. The MITRE Playbook provides detailed guidance on this process, emphasizing that threat models should include abuse cases, misuse scenarios, system constraints, and the needs of all stakeholders including patients, clinicians, and healthcare organizations.
Clinical impact analysis: Unlike traditional IT risk assessments that focus primarily on confidentiality, integrity, and availability, medical device risk assessments must evaluate potential patient harm. This includes both direct harm from security failures and indirect harm from security controls that impede clinical care. The analysis must consider various clinical scenarios, from routine procedures to emergency situations.
Risk categorization framework: Medical devices require sophisticated risk categorization that accounts for both cybersecurity risks and clinical risks. High-risk scenarios might include life-supporting devices in emergency situations, while lower-risk scenarios might involve diagnostic devices used in routine care. This categorization drives the selection and implementation of appropriate security controls.
Usability Risk Assessment Integration
Parallel to security risk assessment, manufacturers must conduct thorough usability risk assessments that evaluate how security controls impact clinical workflows and patient safety. This dual assessment approach is essential for achieving optimal medical device cybersecurity usability.
Use environment analysis: Medical devices operate in diverse environments with varying constraints and requirements. Operating rooms have different security needs than patient rooms, and emergency departments present unique challenges compared to outpatient clinics. The use environment analysis must consider physical constraints, workflow patterns, user stress levels, and time pressures specific to each setting.
User capability assessment: Healthcare professionals represent a diverse user base with varying technical skills, physical capabilities, and cognitive loads. Security controls must accommodate this diversity while maintaining effectiveness. The assessment should consider factors such as visual acuity, manual dexterity, cognitive load during high-stress situations, and familiarity with technology.
Workflow impact evaluation: Security controls inevitably impact clinical workflows, and these impacts must be carefully evaluated to prevent unintended consequences. The evaluation should map security controls to specific workflow steps, identify potential bottlenecks or delays, and assess the likelihood of workaround behaviors that could compromise either security or patient safety.
Balanced Control Selection Strategy
The culmination of dual risk assessment is the selection of security controls that optimize both cybersecurity protection and clinical usability. This requires sophisticated decision-making frameworks that can balance competing priorities and constraints.
Tiered authentication approaches: Rather than applying uniform authentication requirements across all device functions, successful implementations use tiered approaches that match authentication strength to risk levels and clinical contexts. High-risk functions like drug dosing calculations might require strong authentication, while basic monitoring functions might use lighter-weight approaches. Emergency situations might trigger special authentication modes that prioritize speed while maintaining audit trails.
Context-aware security: Modern medical devices can implement context-aware security that adapts to clinical situations. For example, devices might recognize emergency codes and automatically adjust security postures, or they might use environmental sensors to detect high-stress situations and modify authentication requirements accordingly. This approach maintains security while accommodating the dynamic nature of healthcare delivery.
Compensating controls: When traditional security controls prove incompatible with clinical requirements, compensating controls can provide alternative protection mechanisms. These might include enhanced monitoring and alerting systems, physical security measures, or procedural controls that achieve security objectives through different means. The FDA specifically recommends that manufacturers assess and provide users with compensating controls to mitigate patient harm risks.
Implementation Strategies
Security Built-In Philosophy
The FDA’s emphasis on security being “built in” rather than “bolted on” becomes particularly critical when addressing medical device cybersecurity usability. This philosophy requires fundamental changes to how manufacturers approach device design and development processes.
Early design integration: Security and usability considerations must be integrated from the earliest stages of device design. This includes incorporating cybersecurity requirements into design inputs as required by 21 CFR 820.30(c), and ensuring that security architects work closely with human factors engineers throughout the development process. Early integration prevents the common problem of security controls that feel like afterthoughts and disrupt clinical workflows.
Architecture considerations: The security architecture must be designed with clinical usability as a primary constraint. This might involve distributed security models that push authentication to less time-critical moments, or hierarchical security structures that provide different access levels based on clinical roles and situations. The architecture should also consider how security controls will scale and adapt as clinical workflows evolve.
Verification approaches: Traditional security verification focuses on confirming that controls work as designed, but medical device verification must also confirm that controls don’t interfere with clinical effectiveness. This requires specialized testing approaches that simulate clinical environments and evaluate both security effectiveness and usability under realistic conditions. The verification process should include clinical simulation testing with actual healthcare professionals.
Emergency Access Provisions
Emergency access represents one of the most challenging aspects of medical device cybersecurity usability. Healthcare emergencies demand immediate device access, but security controls cannot simply be bypassed without creating significant vulnerabilities.
Break-glass procedures: Effective break-glass procedures provide emergency access while maintaining security oversight. These procedures should be clearly defined, well-documented, and regularly tested. They typically involve temporary elevation of access privileges with enhanced monitoring and mandatory post-incident review. The procedures must be simple enough to execute under extreme stress while comprehensive enough to prevent abuse.
Fallback modes: Medical devices should include fallback modes that maintain essential functionality even when primary security systems fail or when emergency access is required. These modes might provide limited functionality with enhanced monitoring, or they might operate with alternative authentication methods that are faster but still secure. The key is ensuring that patient care can continue while maintaining appropriate security oversight.
Audit trails: Emergency access must be accompanied by comprehensive audit trails that document who accessed the device, when, why, and what actions were taken. These trails serve both security and clinical quality purposes, enabling post-incident analysis and continuous improvement of emergency procedures. The audit system must be tamper-resistant and capable of operating even during system failures.
Usability Testing Integration
Successful medical device cybersecurity usability requires extensive testing that evaluates both security effectiveness and clinical usability under realistic conditions. This testing must be integrated throughout the development process, not relegated to final validation phases.
Clinical simulation testing: Security controls must be tested in simulated clinical environments that replicate the stress, time pressure, and complexity of actual healthcare delivery. This testing should involve actual healthcare professionals performing realistic clinical tasks while security controls are active. The testing must evaluate not only whether security controls work, but whether they interfere with clinical effectiveness or encourage dangerous workaround behaviors.
User feedback loops: Continuous feedback from clinical users is essential for optimizing the balance between security and usability. This feedback should be systematically collected, analyzed, and incorporated into design improvements. The feedback process should include formal usability studies as well as ongoing monitoring of how devices are actually used in clinical practice.
Iterative refinement: The balance between security and usability is rarely achieved on the first attempt. Successful implementations use iterative refinement processes that continuously adjust security controls based on real-world experience and changing clinical needs. This process must be supported by robust change control procedures that ensure security is maintained while usability is improved.
Regulatory Compliance and Documentation
FDA Expectations and Requirements
The FDA’s cybersecurity guidance establishes clear expectations for how manufacturers should address medical device cybersecurity usability in premarket submissions. These requirements reflect the agency’s recognition that cybersecurity is an integral component of device safety and effectiveness.
Premarket submission requirements: Under the updated cybersecurity guidance, manufacturers must provide comprehensive documentation of their cybersecurity risk management processes, including how they balanced security controls with clinical usability. This documentation must demonstrate that the selected security controls provide reasonable assurance of safety and effectiveness while maintaining clinical utility. The submission should include detailed analysis of how security controls impact clinical workflows and what measures were taken to minimize negative impacts.
Risk management documentation: The FDA requires extensive documentation of cybersecurity risk management activities, including threat modeling, risk assessment, and control selection rationale. For medical device cybersecurity usability, this documentation must explicitly address how usability considerations influenced security control selection and implementation. The documentation should trace security controls back to identified threats while also demonstrating consideration of clinical impact.
Design control integration: Cybersecurity considerations must be integrated into design controls as required by 21 CFR 820.30. This includes incorporating cybersecurity requirements into design inputs, ensuring that security controls are properly verified and validated, and maintaining traceability between security requirements and design outputs. The design control documentation must demonstrate that usability considerations were integrated throughout the development process.
Standards Alignment Strategy
Successful regulatory compliance requires alignment with multiple standards that address different aspects of medical device cybersecurity usability. These standards provide frameworks for implementing security controls while maintaining clinical effectiveness.
IEC 62366-1 compliance: The human factors standard IEC 62366-1 provides essential guidance for ensuring that security controls don’t compromise clinical usability. Compliance requires systematic analysis of how security controls affect user interactions, identification of potential use errors related to security features, and validation that security controls don’t introduce unacceptable risks. The standard’s risk management approach must be integrated with cybersecurity risk management to ensure comprehensive coverage.
Security standard integration: Multiple cybersecurity standards apply to medical devices, including IEC 62304 for software lifecycle processes and various NIST frameworks for risk management. These standards must be integrated in ways that support both security objectives and clinical usability requirements. The integration process should identify potential conflicts between standards and establish resolution approaches that prioritize patient safety.
Documentation requirements: Regulatory compliance requires extensive documentation that demonstrates how security and usability requirements were balanced throughout the development process. This documentation must be organized in ways that support regulatory review while also providing practical guidance for ongoing device management. The FDA provides specific recommendations for documentation organization and content that should be followed to ensure compliance.
Practical Examples and Solutions
Authentication Solutions That Work
Real-world implementation of medical device cybersecurity usability requires authentication solutions that balance security strength with clinical practicality. Several approaches have proven effective in different clinical contexts.
Biometric options: Biometric authentication can provide strong security while maintaining clinical efficiency. Fingerprint readers integrated into device interfaces allow rapid authentication without requiring users to remember passwords or carry tokens. However, biometric systems must account for clinical realities such as gloved hands, hand injuries, or emergency situations where the authorized user isn’t available. Successful implementations often combine biometrics with alternative authentication methods for these scenarios.
Multi-factor approaches: Sophisticated multi-factor authentication systems can adapt to clinical contexts while maintaining security. These might combine something the user knows (like a PIN), something they have (like a badge), and something they are (like biometrics). The key is implementing these factors in ways that don’t create clinical bottlenecks. For example, badge-based authentication might be combined with biometrics for high-risk functions while allowing badge-only access for routine monitoring.
Context-based security: Advanced implementations use contextual information to adjust authentication requirements dynamically. A device might require full authentication during normal operations but switch to emergency mode during code situations, requiring only basic identification with enhanced monitoring. Location-based authentication might provide different access levels depending on whether the device is in an ICU versus a general ward.
Interface Design Excellence
The user interface represents the primary interaction point between security controls and clinical workflows, making interface design critical for medical device cybersecurity usability.
Emergency mode UI: Successful devices provide clear visual and auditory indicators when operating in emergency mode with modified security controls. The interface should make it obvious when enhanced monitoring is active and provide clear guidance for post-emergency security procedures. Emergency mode interfaces must be intuitive enough to use under extreme stress while comprehensive enough to maintain security oversight.
Clear security indicators: Users must understand the security status of the device and any actions required to maintain security. This includes clear indicators of authentication status, network connectivity, and any security alerts or warnings. The indicators must be prominent enough to be noticed during routine use but not so intrusive that they interfere with clinical tasks.
Workflow optimization: The interface design should optimize clinical workflows while maintaining security. This might involve grouping security-related functions in logical ways, providing shortcuts for common secure operations, or integrating security controls into existing clinical workflow patterns. The goal is making secure operation feel natural rather than burdensome.
Industry Best Practices
Several best practices have emerged from successful implementations of medical device cybersecurity usability across different types of devices and clinical settings.
Lessons learned: Successful implementations consistently emphasize the importance of early and continuous involvement of clinical users in design and testing processes. They also highlight the value of iterative refinement based on real-world usage patterns and the need for comprehensive training programs that help users understand both security requirements and efficient usage patterns.
Success criteria: Effective implementations establish clear success criteria that measure both security effectiveness and clinical usability. These might include metrics like authentication time, user error rates, clinical workflow efficiency, and security incident frequency. The criteria should be established early in development and used to guide design decisions throughout the process.
Common pitfalls: Several common pitfalls can undermine medical device cybersecurity usability. These include implementing security controls without understanding clinical workflows, failing to provide adequate emergency access procedures, creating authentication requirements that are too complex for high-stress situations, and neglecting to train users on efficient security practices. Awareness of these pitfalls can help manufacturers avoid costly design mistakes.
Conclusion
Achieving optimal medical device cybersecurity usability requires a fundamental shift from viewing security and usability as competing priorities to recognizing them as complementary aspects of device safety and effectiveness. The risk-based approach outlined in this article provides a framework for making informed decisions that protect patients while enabling effective clinical care.
The key principles for success include early integration of security and usability considerations, comprehensive risk assessment that considers both cybersecurity and clinical impacts, implementation of adaptive security controls that respond to clinical contexts, and continuous refinement based on real-world usage patterns. Manufacturers who embrace these principles will be better positioned to create devices that meet both regulatory requirements and clinical needs.
Looking forward, the challenge of medical device cybersecurity usability will only become more complex as devices become more connected and healthcare delivery continues to evolve. Success will require ongoing collaboration between security professionals, human factors engineers, clinical users, and regulatory bodies to develop solutions that protect patients while enabling the full potential of modern medical technology.
For quality, regulatory, and engineering teams working on medical device development, the investment in balanced cybersecurity and usability design pays dividends throughout the product lifecycle. By following the risk-based approaches and best practices outlined in this article, teams can create devices that meet regulatory requirements, satisfy clinical needs, and ultimately improve patient outcomes through both security and usability excellence.
The path forward requires commitment to comprehensive risk assessment, early stakeholder engagement, iterative design refinement, and continuous monitoring of real-world performance. With these elements in place, manufacturers can successfully navigate the complex landscape of medical device cybersecurity usability and deliver products that truly serve both security and clinical objectives.
For more detailed guidance on specific aspects of medical device cybersecurity, explore our comprehensive resources on FDA cybersecurity requirements, security architecture design, threat modeling, and risk assessment methodologies. Additional insights on regulatory compliance can be found in our guides to required FDA documentation and post-market cybersecurity responsibilities.