Medical Device Cybersecurity Quick-Start Guide
A Comprehensive Guide for Quality, Regulatory, and Engineering Teams
Table of Contents
Chapter 1: Introduction to Medical Device Cybersecurity
Why Cybersecurity is Important
Medical device cybersecurity is critical for any device that contains software, firmware, or programmable logic—not just network-connected devices. According to the FDA's 2023 guidance, cybersecurity considerations apply to all devices with software functions, regardless of their connectivity status. This includes devices with no network connections, as they may still be vulnerable through USB ports, removable media, or other interfaces.
Important Scope Clarification
The FDA's cybersecurity guidance is not limited to network-connected devices. It applies to any device that:
- Contains software, firmware, or programmable logic
- Has a device software function
- Could be vulnerable through any interface (USB, removable media, etc.)
Key Cybersecurity Risks Include:
- Patient Safety: Cyberattacks can disrupt device function, leading to delayed diagnoses or incorrect treatments
- Data Breaches: Protected health information (PHI) can be exposed to unauthorized parties
- System Disruption: Hospital networks can become inoperable, affecting patient care across entire facilities
- Device Integrity: Unauthorized modifications can compromise device effectiveness and safety
Why This Matters Now
Cybersecurity threats to healthcare have become more frequent and severe. According to the FDA's 2023 guidance, cybersecurity incidents have already rendered medical devices and hospital networks inoperable, directly disrupting patient care. The WannaCry ransomware attack affected hospital systems and medical devices globally. Vulnerabilities like URGENT/11 and SweynTooth have led to potential safety concerns across broad ranges of devices that incorporate affected third-party components.
Cybersecurity = Patient Safety
The FDA recognizes that cybersecurity is fundamentally part of device safety and effectiveness. A secure device is a safe and effective device. This means cybersecurity isn't just an IT concern—it's a patient safety imperative that requires attention from quality, regulatory, and engineering teams throughout the entire product lifecycle.
Chapter 2: Regulatory History and Framework
Evolution of FDA Cybersecurity Requirements
First FDA Cybersecurity Guidance
"Content of Premarket Submissions for Management of Cybersecurity in Medical Devices" established the foundation for addressing cybersecurity during device design.
Postmarket Guidance
"Postmarket Management of Cybersecurity in Medical Devices" established requirements for ongoing cybersecurity risk management after devices reach the market.
Legislative Changes
PATCH Act and FDORA introduced significant regulatory changes, including section 524B requirements.
Current Framework
"Cybersecurity in Medical Devices: Quality System Considerations and Content of Premarket Submissions" established the current regulatory framework.
Section 524B of the FD&C Act
"Cyber Device" Definition
Section 524B(c) defines "cyber device" as a device that:
- Includes software validated, installed, or authorized by the sponsor
- Has the ability to connect to the internet
- Contains technological characteristics that could be vulnerable to cybersecurity threats
Legal Requirements for Cyber Devices
- Applies to 510(k), PMA, De Novo, HDE, and PDP submissions
- Requires specific cybersecurity information in premarket submissions
- Mandates Software Bill of Materials (SBOM) for cyber devices
- Establishes legal requirements (not just recommendations) for cybersecurity
FDA Guidance Scope vs. Legal Definition
While section 524B legally defines "cyber devices" with specific criteria including internet connectivity, the FDA's 2023 cybersecurity guidance document applies much more broadly. In the guidance scope section, FDA clarifies that the cybersecurity recommendations apply to:
- All devices with cybersecurity considerations, including but not limited to devices that have a device software function or contain software (including firmware) or programmable logic
- Devices that are NOT network-enabled or contain other connected capabilities
- All types of devices within the meaning of section 201(h) of the FD&C Act, whether or not they require a premarket submission
Key Distinction: The legal requirements of section 524B apply specifically to "cyber devices" as defined above, but the FDA's cybersecurity guidance and recommendations apply to any medical device with software, regardless of connectivity. This means that even air-gapped devices with software must consider cybersecurity in their design and development processes.
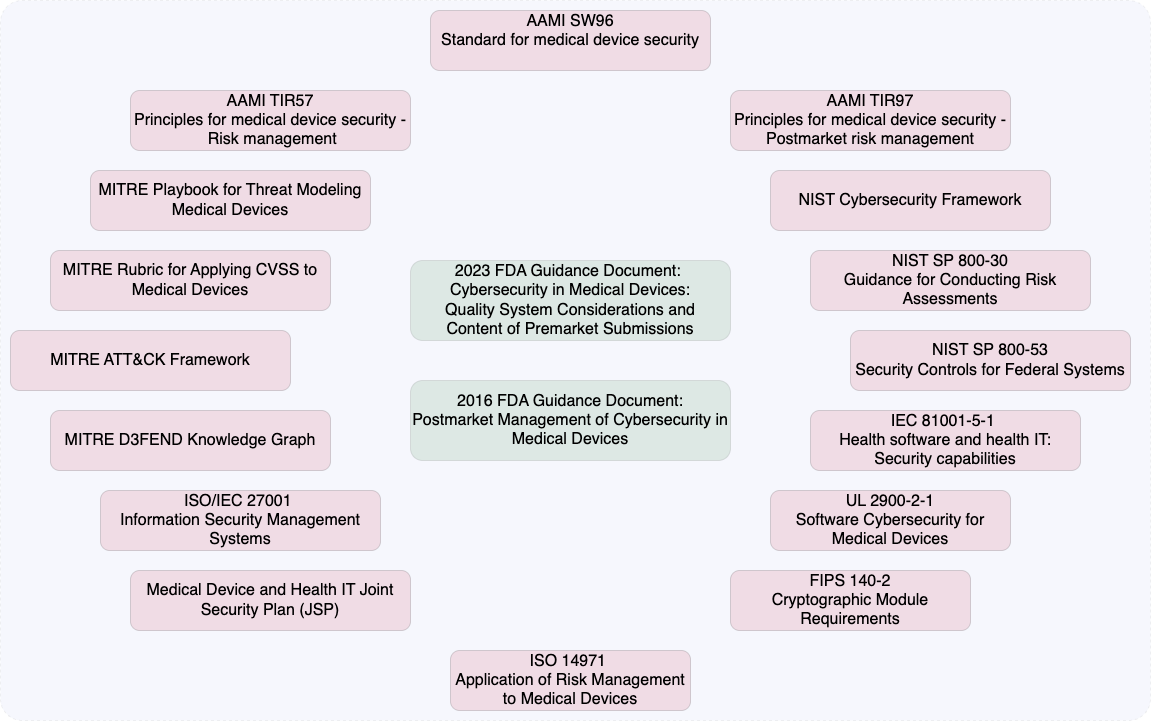
Industry Standards and Framework
While the FDA's cybersecurity guidance documents serve as the primary resource for understanding regulatory expectations, the broader ecosystem of standards and industry resources provides essential context for implementing comprehensive cybersecurity programs. These standards offer detailed methodologies, technical specifications, and best practices that help manufacturers understand the nuanced requirements and proven approaches for ensuring device security and preparing robust regulatory documentation. Many of these standards are specifically referenced or recommended by the FDA, creating an interconnected framework for medical device cybersecurity.
FDA Guidance Documents
- FDA 2023 Cybersecurity Premarket Guidance - Latest requirements for new device submissions
- FDA 2016 Postmarket Cybersecurity Guidance - Managing cybersecurity throughout device lifecycle
Core AAMI Standards
- ANSI/AAMI SW96:2023 - Security risk management for device manufacturers (largely replaces TIR57)
- AAMI TIR97:2019 - Postmarket security risk management principles
- AAMI TIR57:2016/(R)2023 - Principles for medical device security risk management (superseded by SW96, but helpful)
Related Standards
- ISO 14971:2019 - Risk management application to medical devices
- ISO TR 24971:2020 - Guidance on applying ISO 14971
- IEC 62304:2006+A1:2015 - Medical device software lifecycle processes
- IEC 80002-1:2009 - Application of ISO 14971 to medical device software
- ISO 29147:2018 - Vulnerability disclosure processes
- ISO 30111:2013 - Vulnerability handling processes
- ISO 81001-5-1:2021 - Health software security lifecycle activities
- IEC 62366-1 - Usability engineering for medical devices
- UL 2900 series - Software cybersecurity for network-connected products
- IEC 80001-1:2010 - Risk management for IT networks with medical devices
- IEC 80001-2-2:2012 - Communication of medical device security needs
- IEC 62443 series - Industrial cybersecurity standards
- NIST Cybersecurity Framework - Critical infrastructure protection
- NIST SP 800-53 - Security controls for federal systems
- FIPS 140-2 - Cryptographic module requirements
- FIPS 199 - Security categorization standards
- FIPS 200 - Minimum security requirements
Industry Resources
- Medical Device Joint Security Plan v2.0 - Comprehensive security framework
- MITRE Playbook for Threat Modeling Medical Devices - Practical threat modeling guidance
- MITRE Rubric for Applying CVSS to Medical Devices - FDA-qualified MDDT for vulnerability scoring
- MITRE ATT&CK Framework - Adversary tactics, techniques, and procedures
- MITRE D3FEND Knowledge Graph - Defensive countermeasure techniques
- IMDRF Cybersecurity Principles - International harmonization guidance
- MDCG 2019-16 - European cybersecurity guidance
- HIMSS/NEMA MDS2 - Manufacturer disclosure statement
- Health Industry Cybersecurity Practices (HICP) - Sector-specific best practices
- CVSS - Common Vulnerability Scoring System
Comprehensive Ecosystem
This regulatory and standards framework creates a comprehensive ecosystem where FDA requirements, international standards, and industry best practices work together to ensure medical device cybersecurity throughout the product lifecycle. The combination of legally binding requirements and voluntary best practices provides manufacturers with both compliance requirements and practical implementation guidance.
Chapter 3: Planning and Architecting for Security
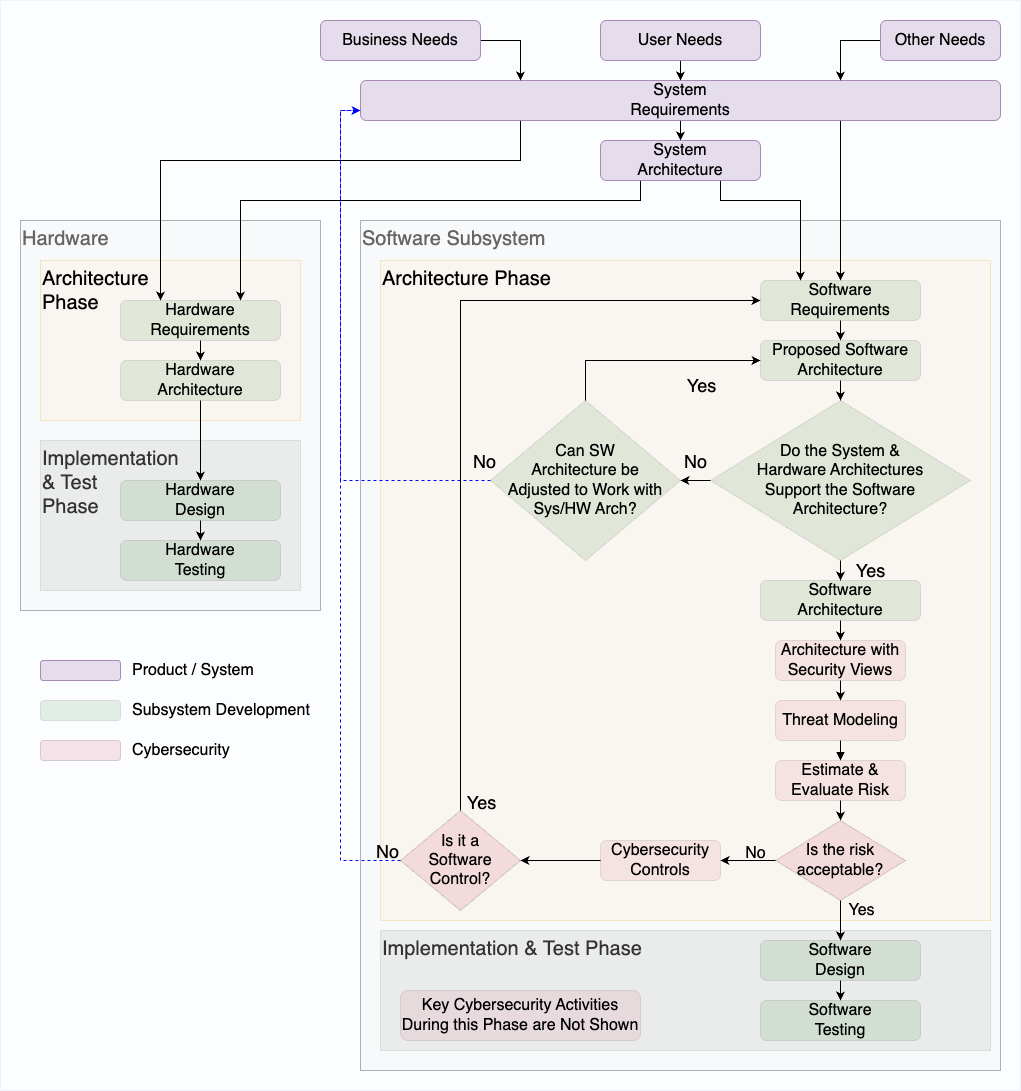
Security Management Plan
A security management plan establishes the foundation for all cybersecurity activities throughout the Total Product Life Cycle (TPLC). This plan should define how security risks will be identified, analyzed, and controlled.
Key Elements
- Security risk management process integration with safety risk management per ISO 14971
- Clear definitions of acceptable vs. unacceptable security risks
- Roles and responsibilities for security activities
- Documentation and review procedures
FDA Security Objectives
Security Objectives per FDA 2023 Guidance
The FDA has established five core security objectives that devices must address:
- Authenticity (which includes integrity): Ensuring information originates from trusted sources
- Authorization: Controlling access to device functions and data
- Availability: Maintaining device functionality when needed for patient care
- Confidentiality: Protecting sensitive data from unauthorized access
- Secure and timely updatability and patchability: Ability to deploy security updates safely
Security Architecture Views
The FDA recommends providing four specific types of architecture views:
Threat Modeling
Systematic Threat Identification
- Create detailed Data Flow Diagrams (DFDs)
- Identify trust boundaries between security domains
- Use structured methodologies like STRIDE
- Consider threats throughout the device lifecycle
Security Risk Assessment
CVSS for Medical Devices
The Common Vulnerability Scoring System (CVSS) provides standardized vulnerability assessment. The MITRE Medical Device CVSS Rubric (FDA-qualified MDDT) provides guidance for scoring CVSS metrics in clinical environments with consideration of patient safety impacts.
Chapter 4: Secure Development
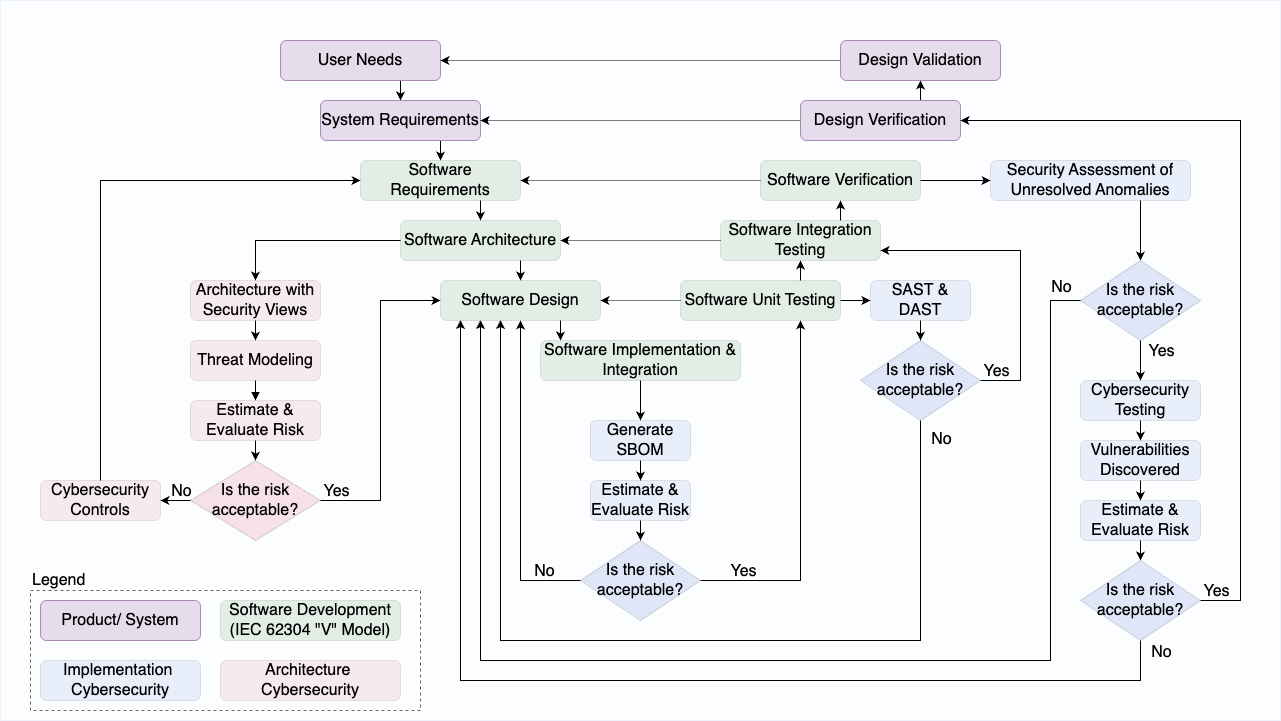
Secure Coding Practices
Essential Secure Coding Elements
- Input Validation: Validate all data entering the system using allowlists
- Memory Management: Use memory-safe languages and implement bounds checking
- Error Handling: Fail securely without exposing sensitive information
- Cryptography: Use proven libraries and current standards
Third-Party Component Evaluation
Modern devices rely heavily on third-party software components. Comprehensive evaluation includes:
- Creating comprehensive Software Bill of Materials (SBOM)
- Assessing known vulnerabilities in CVE, NVD, and CISA KEV Catalog
- Evaluating vendor security practices and support timelines
- Planning for component lifecycle management
Security Testing
Integrated Security Testing Approach
- Static Analysis (SAST): Analyze source code for vulnerabilities
- Dynamic Analysis (DAST): Test running applications
- Fuzz Testing: Provide invalid inputs to identify vulnerabilities
- Penetration Testing: Simulate real-world attacks
SBOM Management
Software Bill of Materials management is required for cyber devices under section 524B:
- Use standardized formats (SPDX, CycloneDX, SWID)
- Include component versions, suppliers, and dependency relationships
- Document known vulnerabilities and security status
- Maintain throughout the product lifecycle
Chapter 5: eSTAR Submission Artifacts
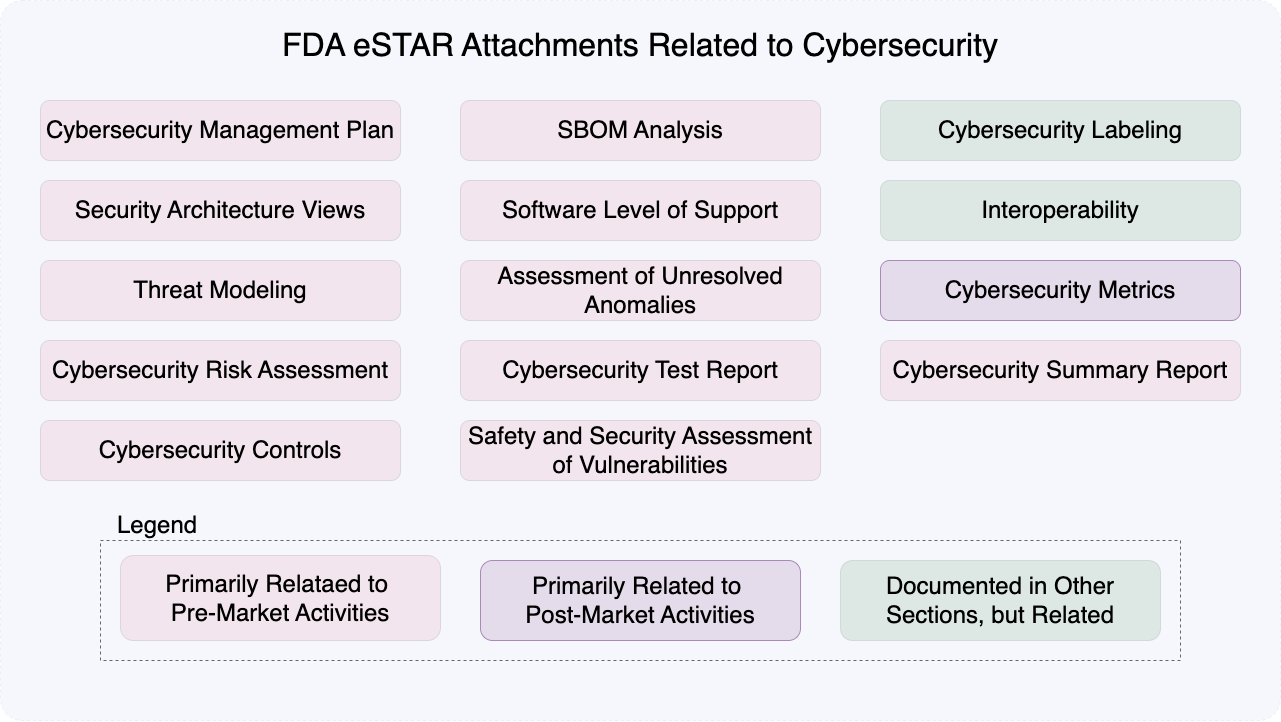
Legal Requirements vs. Recommendations
Under section 524B of the FD&C Act, certain cybersecurity documentation is legally required for cyber devices. FDA requires additional documentation per their 2023 guidance. While the additional documents may seem like recommendations, FDA is likely to issue deficiencies if any of them are missing.
Required Documentation
Security Architecture Views
Security architecture views communicate the security design to FDA reviewers and demonstrate how security controls are implemented throughout the system. These views must scale based on the cybersecurity risk of the device.
FDA-Required Architecture Views
The FDA recommends providing, at minimum, the following four types of views:
Documentation Requirements for Architecture Views
- Clear, detailed diagrams with appropriate level of detail for system complexity
- Explanatory text describing security design decisions and rationale
- Identification of security-relevant system elements and their interfaces
- Definition of security context, domains, boundaries, and critical user roles
- Mapping to security requirements, controls, and threat model findings
- Traceability to risk assessment results and security objectives
- Consistency across all architectural views with cross-references where appropriate
- Alignment with security objectives and requirements to address identified threats
- Protocol details of communication pathways including authentication and session management
- Sufficient detail for engineers and reviewers to follow data, code, and commands through the system
Threat Model Documentation
The threat model demonstrates systematic identification and analysis of security threats specific to the device and its operating environment. This documentation provides the foundation for risk assessment and security control selection.
Data Flow Diagrams (DFDs)
- Complete system decomposition showing all processes, data stores, and external entities
- Trust boundaries clearly marked and explained with security implications
- Data flows labeled with security-relevant information and protection requirements
- Appropriate level of detail for the system complexity and attack surface
- Multiple diagram levels (high-level system view and detailed component views)
- Clear notation and legend explaining all symbols and conventions used
- Integration points with external systems and their security implications
Threat Identification and Analysis
- Systematic threat enumeration for each system element using structured methodologies
- Use of proven frameworks (STRIDE, attack trees, cyber attack lifecycle)
- Consideration of threats throughout the device lifecycle including development, deployment, operation, and decommissioning
- Documentation of threat sources, motivations, and capabilities
- Assessment of threat likelihood and potential impact using CVSS or similar frameworks
- Consideration of attacker capabilities, resources, and access levels
- Evaluation of existing security controls against identified threats
- Prioritization of threats based on risk level and potential patient safety impact
- Integration with vulnerability assessments of third-party components
- Regular updates to threat model as new threats emerge or system changes occur
Cybersecurity Risk Assessment
The risk assessment evaluates and prioritizes cybersecurity risks to guide security control implementation. This analysis forms the basis for all security-related design decisions and control selection.
Risk Analysis Methodology
- Clear description of risk assessment approach used (CVSS, NIST SP 800-30, OWASP, etc.)
- Detailed criteria for likelihood and impact evaluation with scoring rationale
- Risk scoring methodology with examples and consistency checks
- Integration with safety risk management processes per ANSI/AAMI SW96
- Consideration of intelligent adversaries and adaptive threats
- Assessment of cascading effects and system-wide impacts
- Evaluation of residual risks after control implementation
Risk Register and Documentation
- Comprehensive list of identified security risks with unique identifiers
- Risk likelihood and impact assessments with supporting rationale
- Current risk levels and risk treatment decisions
- Mapping to security controls, mitigations, and compensating measures
- Traceability to threat model findings and system vulnerabilities
- Risk ownership assignments and management responsibilities
- Risk monitoring and review processes with defined frequencies
- Application of risk acceptability criteria with approval documentation
- Documentation of risk treatment decisions and alternatives considered
- Identification and assessment of residual risks remaining after treatment
Security Controls Documentation
Document all implemented security controls and their effectiveness per the FDA's recommended security control categories. This documentation demonstrates how security objectives are achieved through specific technical and operational measures.
Required Security Control Categories
Per FDA 2023 guidance, security controls must address these eight categories:
- Authentication: Verifying identity of users, processes, and devices with specific mechanisms and protocols
- Authorization: Granting appropriate access privileges based on roles and least privilege principles
- Cryptography: Protecting data and communications using encryption with algorithm specifications
- Code, Data, and Execution Integrity: Ensuring software and data haven't been tampered with
- Confidentiality: Protecting sensitive information from unauthorized disclosure
- Event Detection and Logging: Monitoring and recording security-relevant events
- Resiliency and Recovery: Maintaining functionality and recovering from attacks
- Updatability and Patchability: Securely deploying software updates and security patches
Control Documentation Requirements
- Complete catalog of implemented security controls mapped to the eight categories
- Detailed control descriptions and implementation specifications
- Mapping to security requirements, risks, and threat model findings
- Control verification and testing evidence with test results
- Traceability to architecture views and system design decisions
- Performance impact assessment of security controls on device functionality
- Integration testing results showing controls work together effectively
- Configuration management procedures for security controls
- Monitoring and maintenance procedures for ongoing control effectiveness
- Failure mode analysis and backup procedures for critical security controls
Safety and Security Risk Integration Analysis
Demonstrates how security and safety risks have been properly integrated and managed throughout the development process. This analysis ensures that cybersecurity threats to safety are properly addressed and that safety controls don't inadvertently create security vulnerabilities.
Security-to-Safety Analysis
- Identification of security risks that could lead to safety hazards with impact assessment
- Transfer of appropriate risks to safety risk management per ISO 14971
- Integration of security considerations into safety analysis and FMEA processes
- Verification that safety controls adequately address security-related hazards
- Documentation of safety risk acceptability decisions for security-related hazards
- Traceability between security vulnerabilities and potential patient harm scenarios
Safety-to-Security Analysis
- Assessment of how safety controls might impact security (e.g., emergency overrides bypassing authentication)
- Evaluation of emergency override procedures and their security implications
- Analysis of fail-safe modes and their security implications
- Consideration of maintenance and service access impacts on security
- Assessment of physical safety features that might affect cybersecurity
- Documentation of compensating security measures for safety-required exceptions
Combined Risk Assessment
- Integrated view of safety and security risks with interaction analysis
- Analysis of risk interactions, dependencies, and cascading effects
- Overall risk evaluation and acceptability assessment
- Coordinated risk treatment strategies addressing both safety and security concerns
- Unified risk monitoring and review processes
- Cross-functional team coordination between safety and security risk management
Cybersecurity Management Plan
The management plan describes how cybersecurity will be managed throughout the Total Product Life Cycle (TPLC). For cyber devices, this plan is required under section 524B(b)(1) of the FD&C Act and must demonstrate ongoing commitment to device security.
Required Elements per FDA 2023 Guidance
- Personnel responsible for cybersecurity activities with roles and responsibilities defined
- Sources, methods, and frequency for monitoring and identifying vulnerabilities
- Process to identify and address vulnerabilities in the CISA Known Exploited Vulnerabilities Catalog
- Periodic security testing schedules and procedures with defined frequencies
- Timeline to develop and release patches based on vulnerability severity
- Update processes and delivery mechanisms with customer communication plans
- Patching capability assessment (rate at which updates can be delivered to devices)
- Description of coordinated vulnerability disclosure process following ISO 29147:2018
- Communication plans for remediations, patches, and updates to customers
- Integration with existing quality management and change control systems
Organizational and Process Elements
- Governance structure and decision-making authority for cybersecurity issues
- Resource allocation and budget considerations for ongoing cybersecurity activities
- Training and competency requirements for cybersecurity personnel
- Integration with quality management systems and design controls
- Incident response procedures and escalation processes
- Vendor and supplier security management requirements
- Customer support procedures for security-related issues
- End-of-life planning and secure device retirement procedures
SBOM Analysis and Documentation
Software Bill of Materials documentation provides transparency about software components and their security status. This is required for cyber devices under section 524B and must be maintained throughout the device lifecycle.
SBOM Content Requirements
- Complete inventory of software components including proprietary, COTS, and open-source
- Component version information and supplier details with contact information
- Dependency relationships and hierarchies showing transitive dependencies
- License information and usage rights with compliance requirements
- Known vulnerabilities and security status using CVE identifiers
- Integrity verification information (cryptographic hashes) for component authentication
- Component criticality assessment and impact on device functionality
- Update frequency and availability of security patches for each component
Vulnerability Analysis and Management
- Assessment of known vulnerabilities in components using CVE, NVD, and CISA KEV Catalog
- Evaluation of vulnerability impact on device security using CVSS or similar frameworks
- Risk assessment for vulnerable components with exploitability analysis
- Mitigation strategies for unpatched vulnerabilities with compensating controls
- Vendor response analysis and patch availability assessment
- Component replacement planning for end-of-life or unsupported software
- Continuous monitoring procedures for new vulnerabilities in existing components
Component Support Status and Lifecycle Management
- Supplier support commitments and service level agreements
- End-of-life schedules for components with transition planning
- Update and patching capabilities with deployment procedures
- Alternative components and migration plans for critical dependencies
- Vendor relationship management and communication procedures
- Budget and resource planning for component updates and transitions
Software Level of Support Assessment
Document the support status and implications for all software components throughout their lifecycle. This assessment helps identify risks associated with component support levels and plan for necessary transitions.
Support Classification and Assessment
- Categorization of all components by support level (supported, limited, end-of-life, community, custom)
- Vendor support commitments and service level agreements with contact procedures
- Community support assessment for open-source components including maintainer activity
- Internal support capabilities for custom components with knowledge management
- Support cost analysis and budget planning for ongoing maintenance
- Support quality assessment based on vendor track record and response times
Risk Assessment and Mitigation
- Security risks associated with each support level with impact analysis
- Impact of end-of-life components on device security and functionality
- Mitigation strategies for unsupported components with compensating controls
- Long-term sustainability planning with component roadmaps
- Risk acceptance decisions and approval documentation for unsupported components
- Monitoring procedures for security issues in unsupported components
Lifecycle Management and Transition Planning
- Component monitoring and update processes with defined procedures
- Transition planning for end-of-life components with timelines and milestones
- Vendor relationship management and communication strategies
- Budget and resource planning for component updates and migrations
- Change control procedures for component transitions
- Testing and validation procedures for component updates and replacements
Assessment of Unresolved Anomalies
Documentation of how security-relevant anomalies discovered during development have been evaluated and managed. This assessment demonstrates that all potential security issues have been properly considered and addressed.
Anomaly Documentation and Classification
- Complete list of unresolved anomalies with potential security relevance and unique identifiers
- Analysis of potential security impacts using structured methodologies and impact assessment
- Risk assessment for each anomaly using CVSS or similar frameworks
- Justification for leaving anomalies unresolved with supporting rationale and approval
- Classification by security relevance (security-relevant, safety-relevant, functional, performance)
- Traceability to discovery methods and original test cases or findings
- Impact analysis on overall system security posture
Compensating Controls and Risk Mitigation
- Compensating controls implemented to mitigate anomaly-related risks
- Monitoring procedures for detecting issues related to known anomalies
- Detection and response procedures for anomaly-related security events
- Customer communication about known limitations and required precautions
- User training recommendations for working around known anomalies
- Plans for future resolution including timelines and resource requirements
- Risk acceptance documentation and approval by appropriate authority
Cybersecurity Test Reports
Comprehensive documentation of all cybersecurity testing activities and their results. This report demonstrates that security controls have been properly implemented and validated through appropriate testing methodologies.
Testing Scope and Methodology
- Description of testing approach and objectives for all security testing performed
- Test environment configuration and any constraints or limitations
- Testing tools and techniques used (SAST, DAST, fuzzing, penetration testing)
- Test case development and execution procedures with traceability to requirements
- Testing team qualifications and independence considerations
- Testing schedule and integration with development milestones
- Test data management and privacy protection procedures
Test Results and Analysis
- Detailed results from all security testing activities with evidence
- Vulnerabilities discovered during testing and their resolution status
- Verification evidence that security requirements have been met
- Performance impact assessment of implemented security controls
- False positive analysis and validation of findings
- Regression testing results after vulnerability remediation
- Integration testing results showing security controls work together effectively
Test Coverage and Validation
- Test coverage analysis mapping tests to security requirements and threat model scenarios
- Coverage analysis for code, functional, and architectural testing
- Identification of any testing gaps with rationale and risk assessment
- Rationale for testing limitations and constraints
- Validation of test effectiveness and adequacy
- Comparison with industry best practices and standards
- Recommendations for ongoing testing and continuous improvement
Cybersecurity Metrics and Monitoring Plans
Establishment of metrics for ongoing cybersecurity monitoring and continuous improvement. These metrics provide measurable indicators of security program effectiveness and enable data-driven security decisions.
Security Performance Indicators
- Metrics for measuring security control effectiveness with baselines and targets
- Incident detection and response time metrics with performance thresholds
- Vulnerability management metrics (time to discovery, remediation, etc.)
- User security behavior metrics where applicable
- Security testing coverage and effectiveness metrics
- Patch deployment success rates and timelines
- Security training completion and effectiveness metrics
- Third-party security assessment and audit results
Monitoring and Reporting Procedures
- Data collection and analysis procedures for ongoing monitoring
- Automated monitoring tools and alert thresholds
- Reporting frequency, stakeholders, and escalation procedures
- Trend analysis and improvement identification processes
- Integration with quality management systems and continuous improvement
- Dashboard and visualization requirements for security metrics
- Data retention and archival procedures for security metrics
- Regular review and update procedures for metrics and thresholds
Cybersecurity Summary Report
A high-level summary that provides FDA reviewers with an overview of the device's cybersecurity posture. This executive summary ties together all cybersecurity documentation and demonstrates overall security adequacy.
Executive Summary and Overview
- Overview of device security architecture with key design decisions
- Key security controls and their rationale with effectiveness demonstration
- Major security risks and their mitigation strategies
- Compliance with relevant standards and guidelines (SW96, TIR97, etc.)
- Integration with safety risk management and overall device safety
- Summary of testing results and validation evidence
- Key assumptions and dependencies in the security design
Security Posture Assessment
- Overall assessment of device security with confidence levels
- Comparison to security best practices and industry benchmarks
- Residual risk evaluation and acceptability assessment
- Ongoing security commitments and lifecycle management plans
- Known limitations and required user/environment precautions
- Future security enhancement plans and roadmap
- Lessons learned and recommendations for similar devices
Cybersecurity Labeling
Information that must be provided to users to ensure secure device deployment and operation. This labeling enables healthcare facilities and users to properly integrate and maintain device security throughout its operational life.
Security Configuration Requirements
- Network security requirements and recommendations for deployment environments
- User authentication and access control requirements with role definitions
- Security monitoring and logging recommendations for healthcare facilities
- Incident response and reporting procedures with contact information
- Required security settings and configuration parameters
- Network segmentation and firewall recommendations
- Physical security requirements for device installation and access
User Security Information and Guidance
- Security features explanation and proper usage instructions
- Known security limitations and required compensating measures
- Security update and patching procedures with customer responsibilities
- Contact information for reporting security concerns or incidents
- User training recommendations and security awareness requirements
- Troubleshooting guidance for security-related issues
- Best practices for secure operation and maintenance
Technical Security Details
- Supported cryptographic algorithms and key lengths with compliance standards
- Network ports and protocols used with security implications
- Security certification and compliance information (FIPS, Common Criteria, etc.)
- Interoperability security considerations with other medical devices and IT systems
- Security logging and audit trail capabilities
- Backup and recovery procedures with security considerations
- End-of-life and secure disposal procedures
Interoperability Security Considerations
Documentation of security considerations for device interoperability with other systems and networks. This analysis ensures that security is maintained when the device operates as part of larger healthcare IT ecosystems.
Integration Security Requirements
- Security requirements for systems that will connect to or integrate with the device
- Trust establishment and authentication procedures for system integration
- Data protection measures during information exchange with external systems
- Security boundary management between the device and connecting systems
- Communication protocol security including encryption and integrity protection
- Session management and secure connection establishment procedures
- Error handling and failure mode security for integration scenarios
Standards Compliance and Testing
- Compliance with relevant interoperability security standards (HL7, DICOM, IHE, etc.)
- Security testing results with representative healthcare IT systems
- Known compatibility issues, workarounds, and security implications
- Certification and validation requirements for secure interoperability
- Third-party integration testing and validation procedures
- Ongoing monitoring and maintenance of interoperability security
- Documentation and communication of security requirements to integration partners
Chapter 6: Post-Market Responsibilities
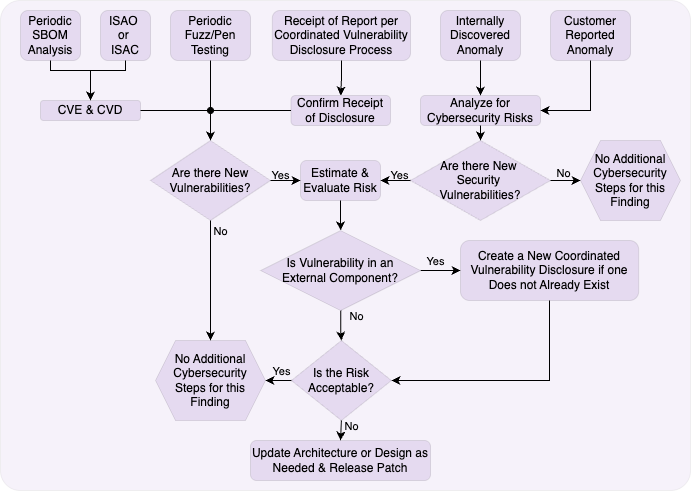
Ongoing SBOM Monitoring
Continuous monitoring of software components for new vulnerabilities:
- Critical vulnerabilities: Monitor continuously (daily)
- High-severity vulnerabilities: Monitor weekly
- CISA Known Exploited Vulnerabilities: Monitor as updates are published
- Automated tools for CVE, NVD, and CISA KEV Catalog monitoring
Coordinated Vulnerability Disclosure
Inbound Vulnerability Reports
- Establish dedicated security reporting channels
- Respond with severity-based timelines (30-120 days based on criticality)
- Follow FDA-recognized standards ISO/IEC 29147:2018 and ISO/IEC 30111:2013
Response Timelines
- Critical vulnerabilities: Remediation within 30 days
- High-severity vulnerabilities: Remediation within 60 days
- Medium-severity vulnerabilities: Remediation within 120 days
Information Sharing
Active participation in cybersecurity information sharing organizations:
- Healthcare Sector ISAC (H-ISAC)
- Medical device security working groups
- Vendor-specific security communities
Security Testing and Updates
- Annual comprehensive penetration testing by external experts
- Quarterly focused testing of specific components
- Continuous fuzzing of critical interfaces
- Regular security update deployment with proper change control
Customer Communication
Effective communication during security events:
- 24-hour notification for critical vulnerabilities with active exploitation
- 5-day notification for high-severity vulnerabilities requiring customer action
- Clear instructions for security updates and patches
- Coordination with healthcare delivery organizations
Key Takeaway
Post-market cybersecurity is an ongoing responsibility that requires continuous monitoring, rapid response capabilities, and effective stakeholder communication to maintain device security throughout the operational lifetime.
Medical Device Cybersecurity Quick-Start Guide
A comprehensive resource for quality, regulatory, and engineering teams implementing FDA cybersecurity requirements.